Interactive Report Summary
Q4 and Full-Year 2023 Cyber Threat Report
Top Findings at a Glance

Ransomware Spotlight: BlackBasta
BlackBasta Ransomware, associated with QakBot malware, escalated its activity by 353.66% in Q4 2023, becoming the second most active ransomware operator. This Russian-speaking operation, suspected to be linked to Conti Ransomware, targets primarily U.S. organizations in financial services, healthcare and commercial facilities.
Since its emergence in 2022, BlackBasta has extorted over $100 million, making it one of the most profitable ransomware strains. The data of organizations that do not pay the ransom is often sold to the highest bidder for further attacks or resale on dark web marketplaces. Unless disrupted by law enforcement, BlackBasta is expected to continue its dominance in the ransomware space.
Methodology
How Nuspire produces its threat intelligence
Hover over tiles to learn more
OCTOBER THROUGH DECEMBER
Q4 2023 in Review
Q4 2023 was marked by numerous software vulnerabilities, the emergence of new malware and a rise in ransomware attacks.
Total Events
Unique Variants
Total Activity
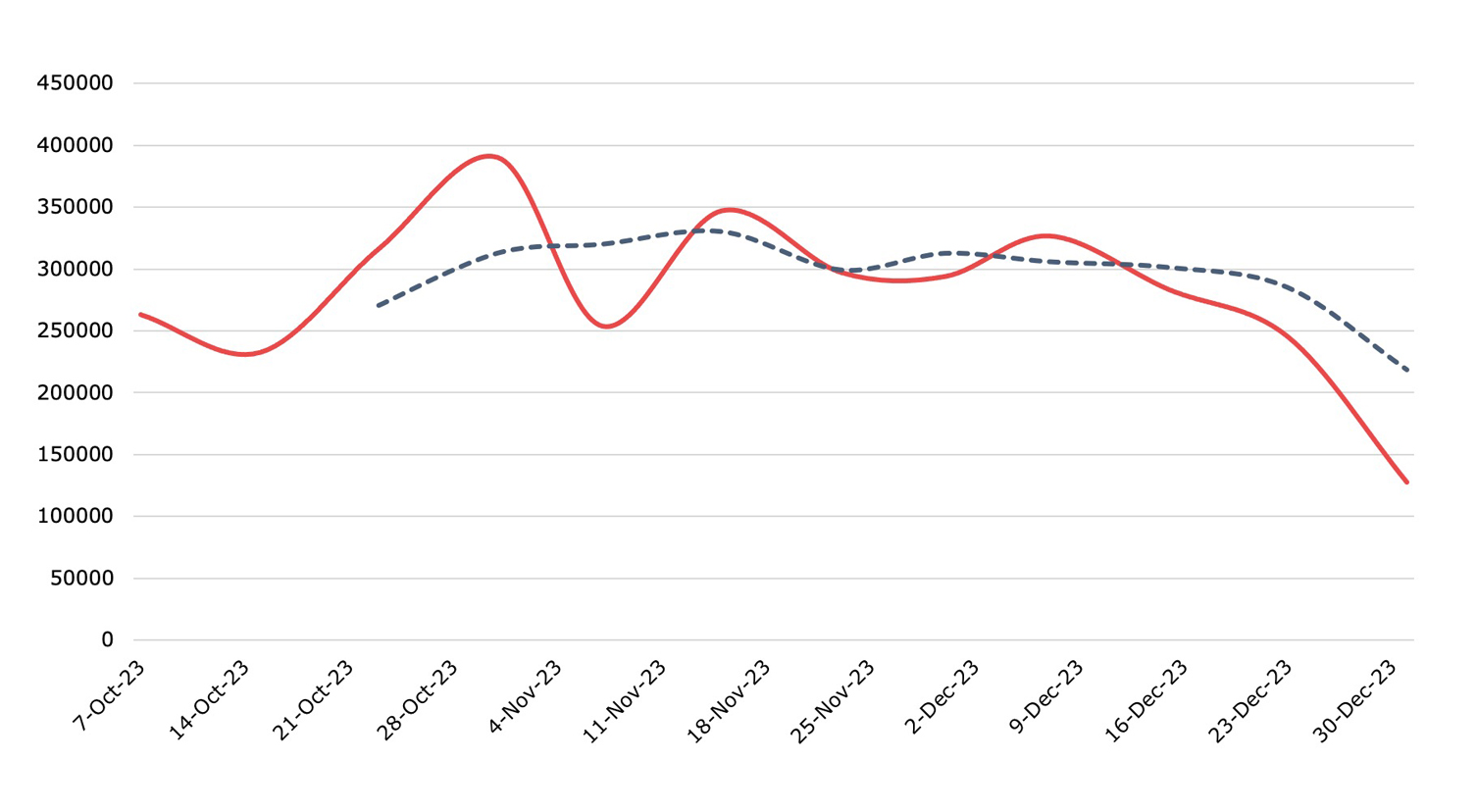
Malware
Detection, Q4 2023Across Nuspire-managed and monitored devices, there was an increase of 88.97% in total malware activity compared to Q3 2023.
How to Combat
To strengthen your defenses against malware activity, you’ll need to adopt a multiprong approach, including endpoint protection platforms and cyber awareness training.
Malware
Malware activity jumped nearly 90% in Q4 2023, buoyed by the extensive use of JavaScript phishing variants and a surge in attacks from ransomware gangs like BlackBasta, which clocked a 354% increase in activity.
Total Events
Unique Variants
Total Activity
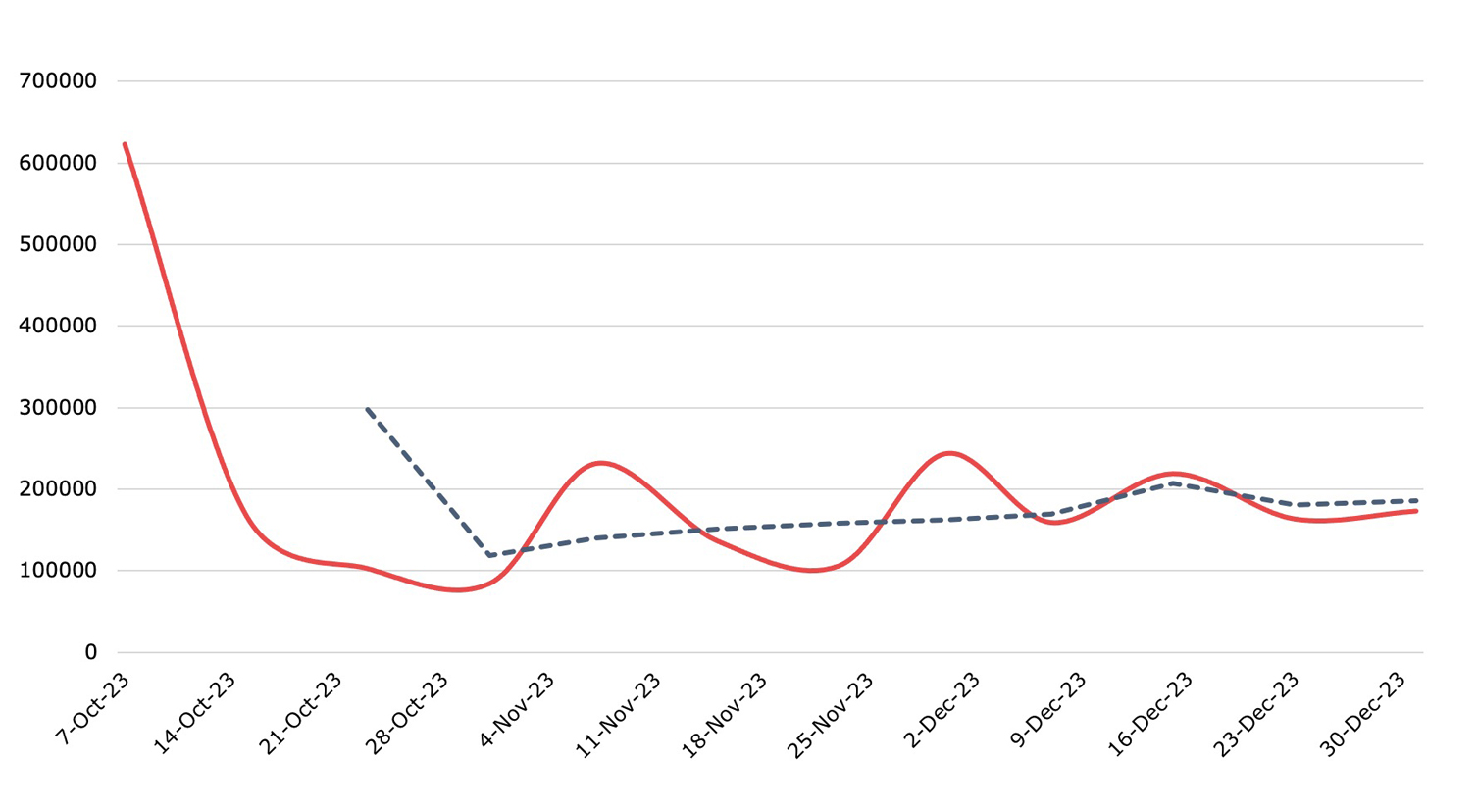
Botnets
Detection, Q4 2023Nuspire saw a slight 6.96% decrease in botnet activity in Q4.
How to Combat
Step up your efforts to stop botnet activity, which is usually detected post-infection. We recommend detecting malicious activity and quarantining devices to minimize botnet spread throughout the network.
Botnets
In Q4, Torpig Mebroot, a top botnet, slowed its activity down significantly, dropping nearly 60% from Q3. In contrast, TorrentLocker, a botnet that re-emerged in Q3, quadrupled its activity. Moreover, Mumblehard, a botnet that targets Linux systems, moved up to fifth place in our Top 5 Botnet list, surpassing Mirai.
Total Events
Unique Variants
Total Activity
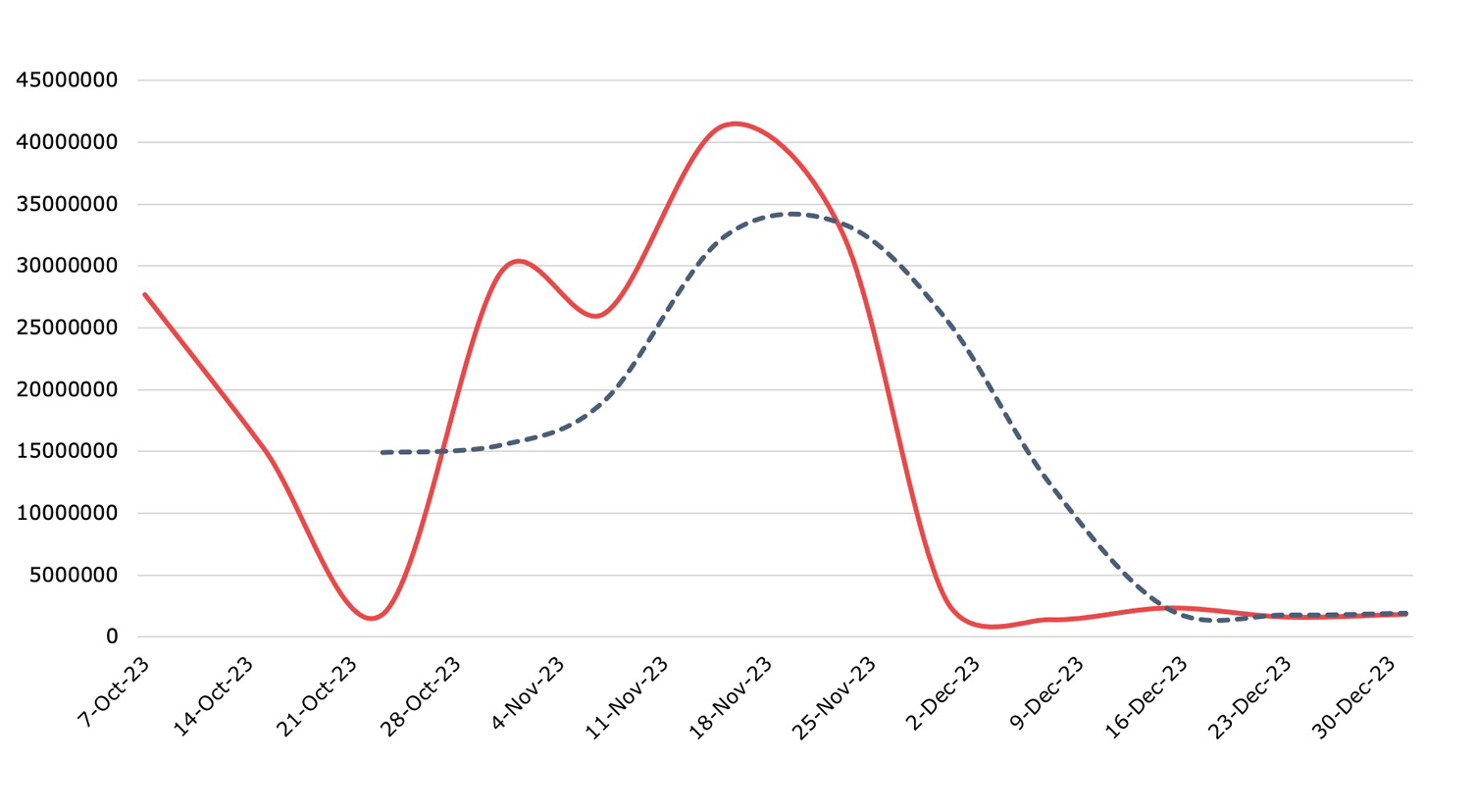
Exploits
Detection, Q4 2023In Q4, exploit activity exploded by 132.91%.
How to Combat
Stop exploits before they do harm by patching systems and security monitoring to thwart attackers and decrease risk.
Exploits
In Q4, Nuspire recorded a substantial surge in exploit activity, with a 132.91% increase primarily fueled by Secure Shell (SSH) brute forcing. A significant shift was observed in threat actor tactics, with a marked 41.64% rise in the use of Web Server Password File Access, an information disclosure exploit, compared to Q3. This exploit has seen a steady uptick each quarter of the year, culminating in a 133.21% increase since Q1.
Stay Vigilant

As Nuspire's Director of Security Operations, Justin Heard is at the helm of the company's key security initiatives, encompassing incident response, threat hunting and cyber intelligence. With over 15 years of experience in cybersecurity, including roles such as threat hunter, incident commander and intelligence analyst, Justin has a deep understanding of the cybersecurity domain. His leadership is instrumental in bolstering Nuspire’s defenses and adapting to the rapidly changing landscape of cyber threats.
Before his tenure at Nuspire, Justin enhanced his skill set in the defense sector, serving as a network administrator and security engineer. Justin has an associate degree in Computer Networking Systems from ITT Tech.

Josh is a Cyber Threat Analyst at Nuspire who works closely in organizational threat landscapes, curating threat intelligence, and authoring Nuspire’s Quarterly Threat Landscape Report. Josh is currently pursuing his master’s degree in Cybersecurity Technology. Previously he served with the U.S. Navy as an Operations Specialist with 14 years of service. Josh has been quoted in Forbes, CSO Online, Channel Futures, Dark Reading, and others.