Interactive Report Summary
Q1 2022 Threat Report
Use of malware, botnets and exploits expands; Mirai sees resurgence
Q1 2022 saw an increase in malware, botnet and exploitation events over Q4 2021. Learn more about the biggest threats we saw, including a slew of new vulnerabilities, in our latest report.
Top Findings at a Glance

Industry Spotlight: Automotive
Automotive continues to be a popular industry target, fending off attacks from Conti Ransomware and Mofang (Superman).
Some of the most popular tactics used by ransomware gangs include spearphishing that leverages malicious Microsoft Office documents, bruteforcing exposed remote desktop protocol, deploying fake software updates and exploiting newly-announced vulnerabilities.
Methodology
Hover over tiles to learn more
Q1 2022 in Review
January through March
Total Events
Unique Variants
Total Activity
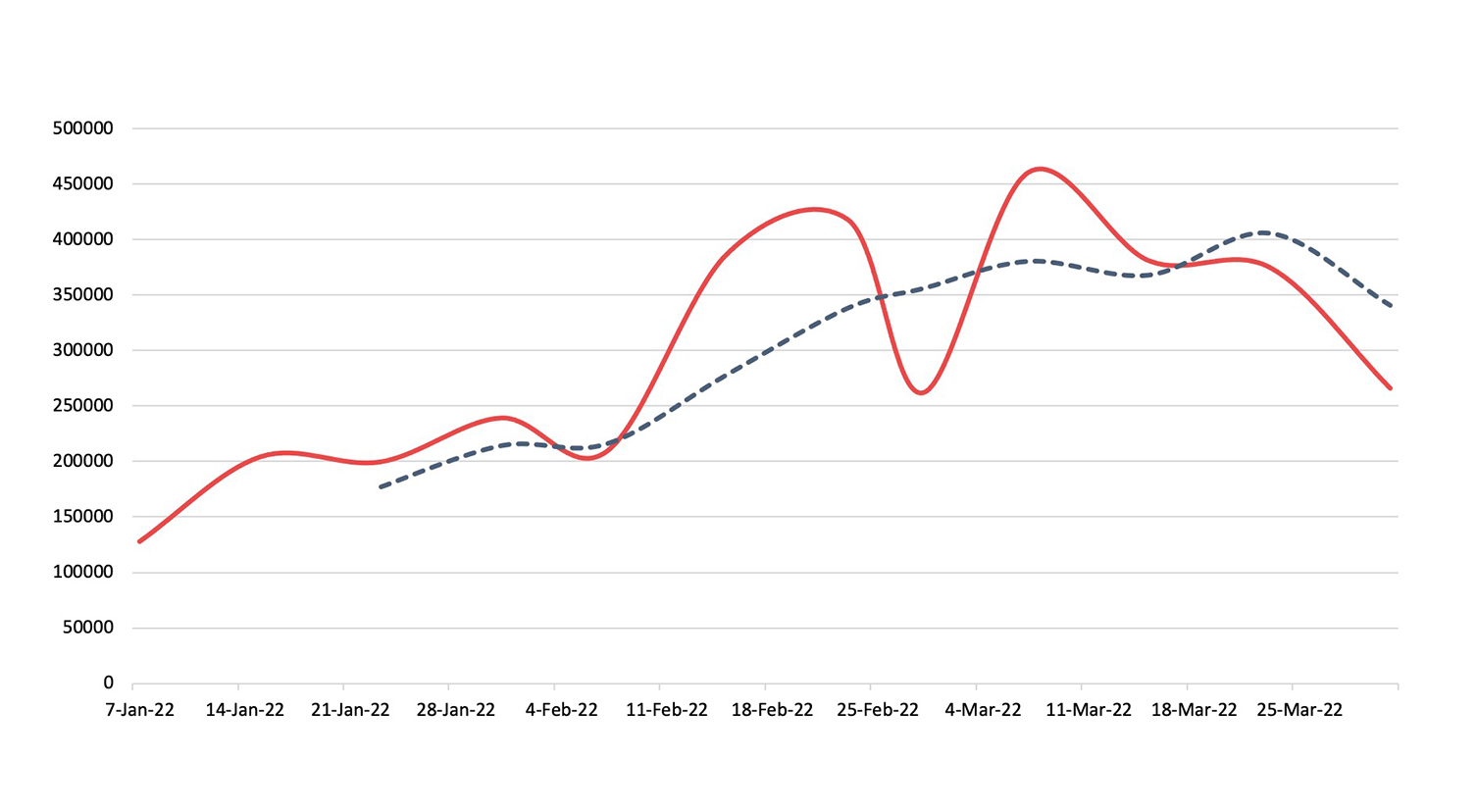
Malware
Detection, Q1 2022Across Nuspire managed and monitored devices, there was an increase of 4.76% in total malware activity compared to Q4 2021.
How to Combat
To strengthen your defenses against malware activity, you’ll need to adopt a multiprong approach including endpoint protection platforms and cyber awareness training.
Malware
As previously witnessed, VBA Agents continue to dominate malware activity; however, Microsoft’s announcement around blocking VBA macros by default on Office products will likely cripple this attack vector.
Total Events
Unique Variants
Total Activity
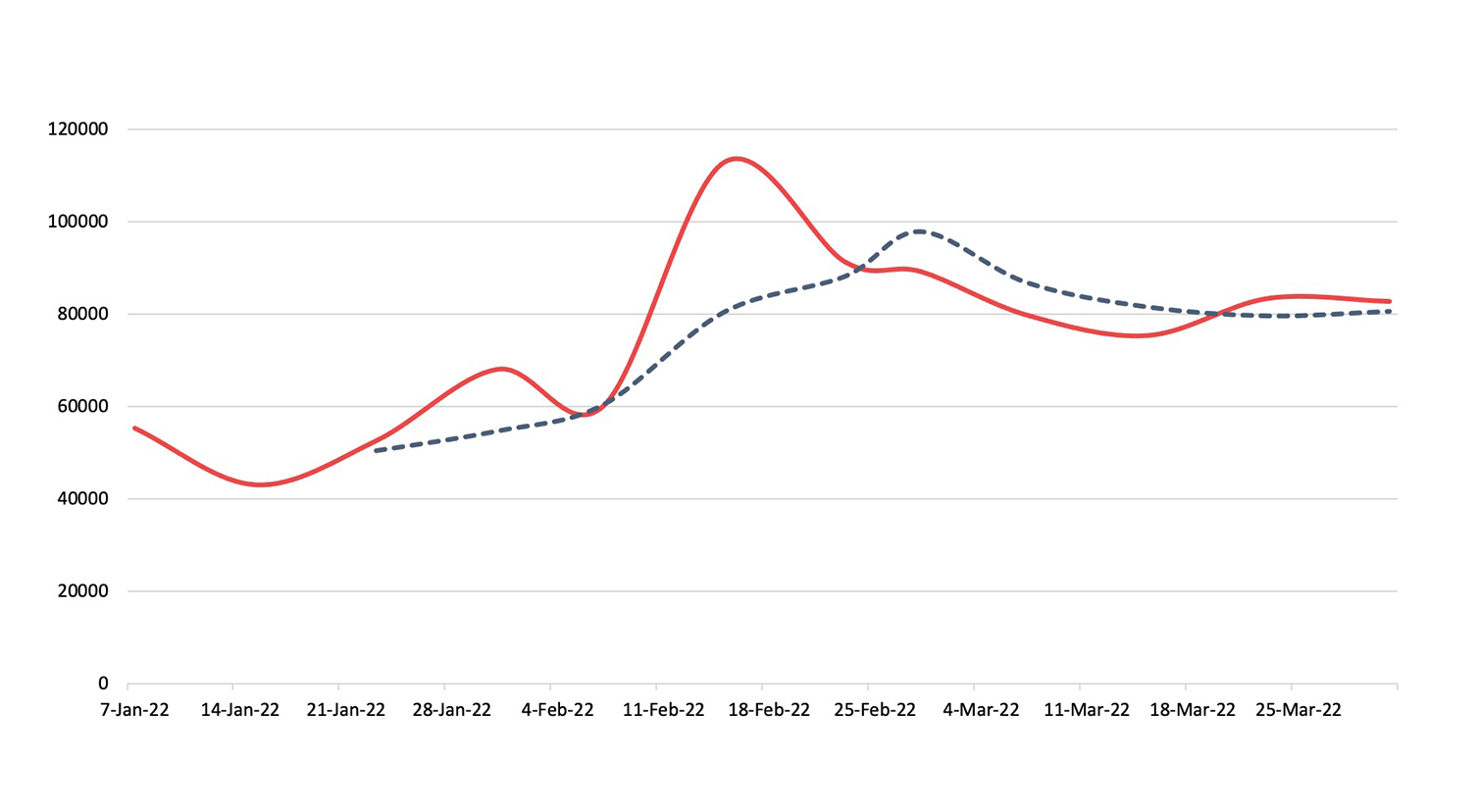
Botnets
Detection, Q1 2022We saw an increase of 12.21% in botnet activity.
How to Combat
Step up your efforts to stop botnet activity, which is usually detected post-infection. We recommend detecting malicious activity and quarantining devices to minimize botnet spread throughout the network.
Botnets
STRRAT botnet came on the scene in Q1 2022. STRRAT contains multiple capabilities such as information stealing, keystroke logging and credential harvesting from browsers and email clients. It is typically deployed via phishing campaigns and uses JavaScript agents and malicious Microsoft Excel files with embedded macros.
Total Events
Unique Variants
Total Activity
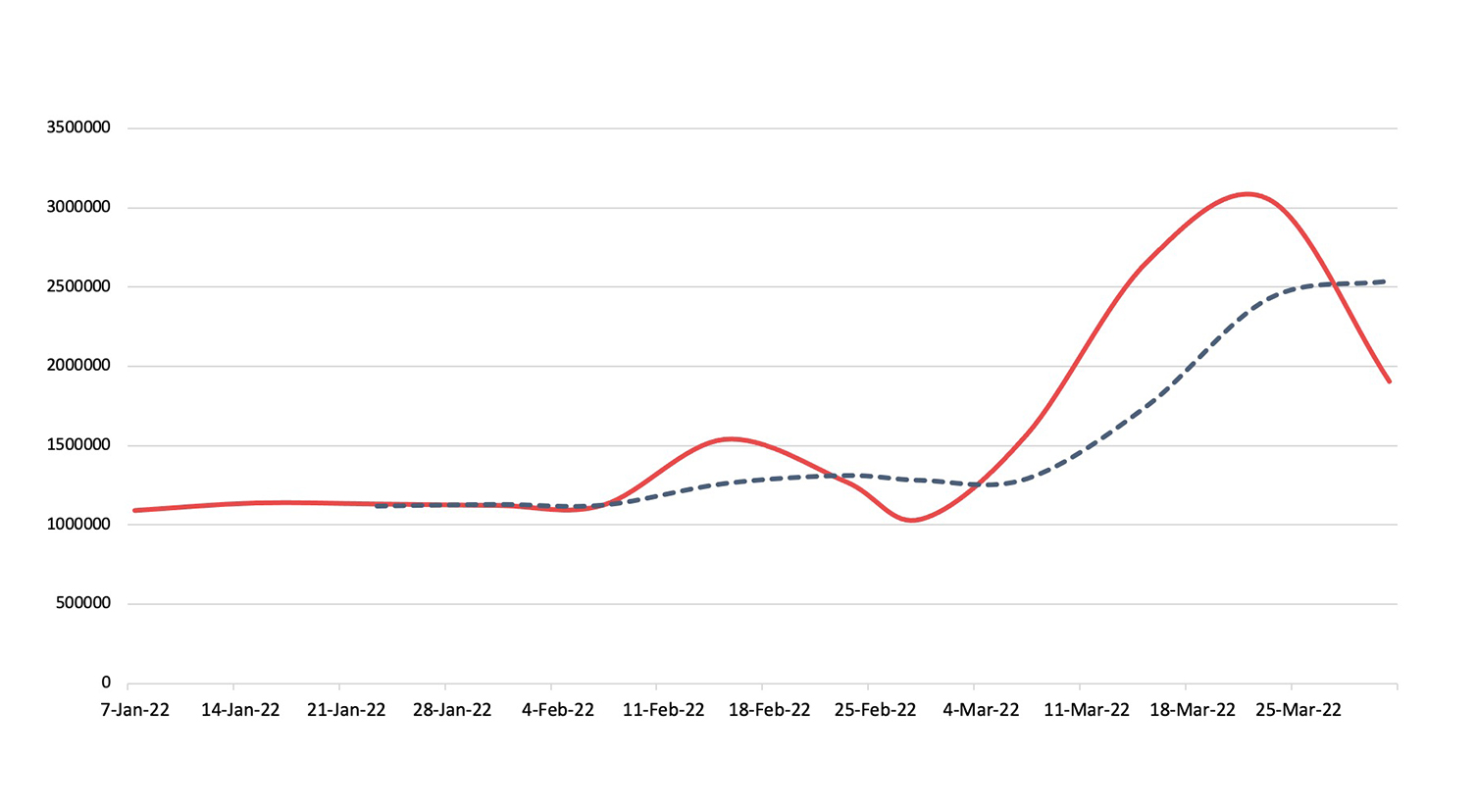
Exploits
Detection, Q1 2022Exploit activity increased by 3.87% over Q4 2021 data, and threat actors focused newly-announced vulnerabilities, especially those with remote code execution (RCE) capabilities.
How to Combat
Stop exploits before they do harm by patching systems and security monitoring to thwart attackers and decrease risk.
Exploits
Bruteforcing was the top exploit in Q1 2022. Threat actors are consistently scanning for exposed services such as SMB and SSH, and if found, will immediately attempt to gain access.