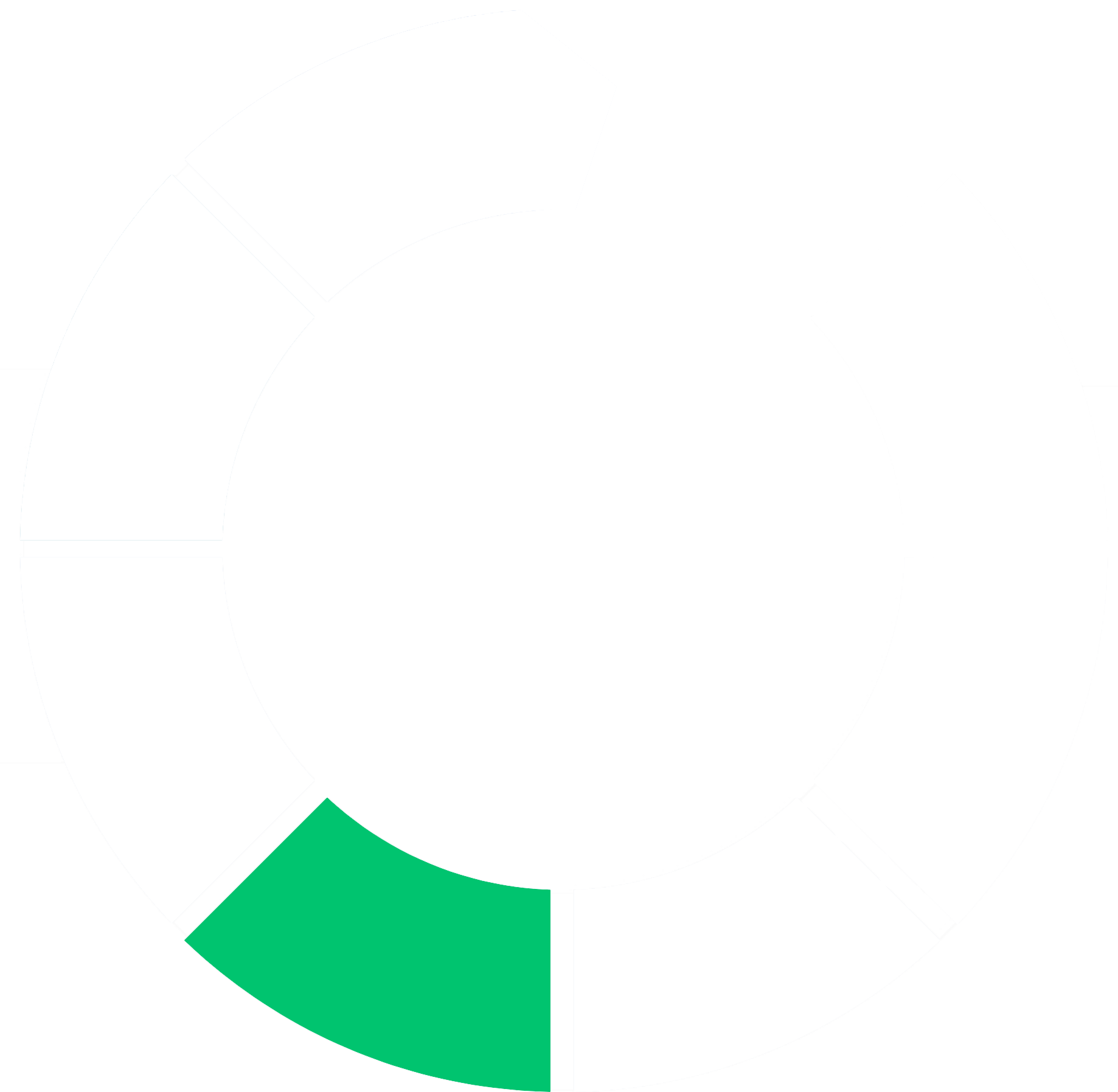
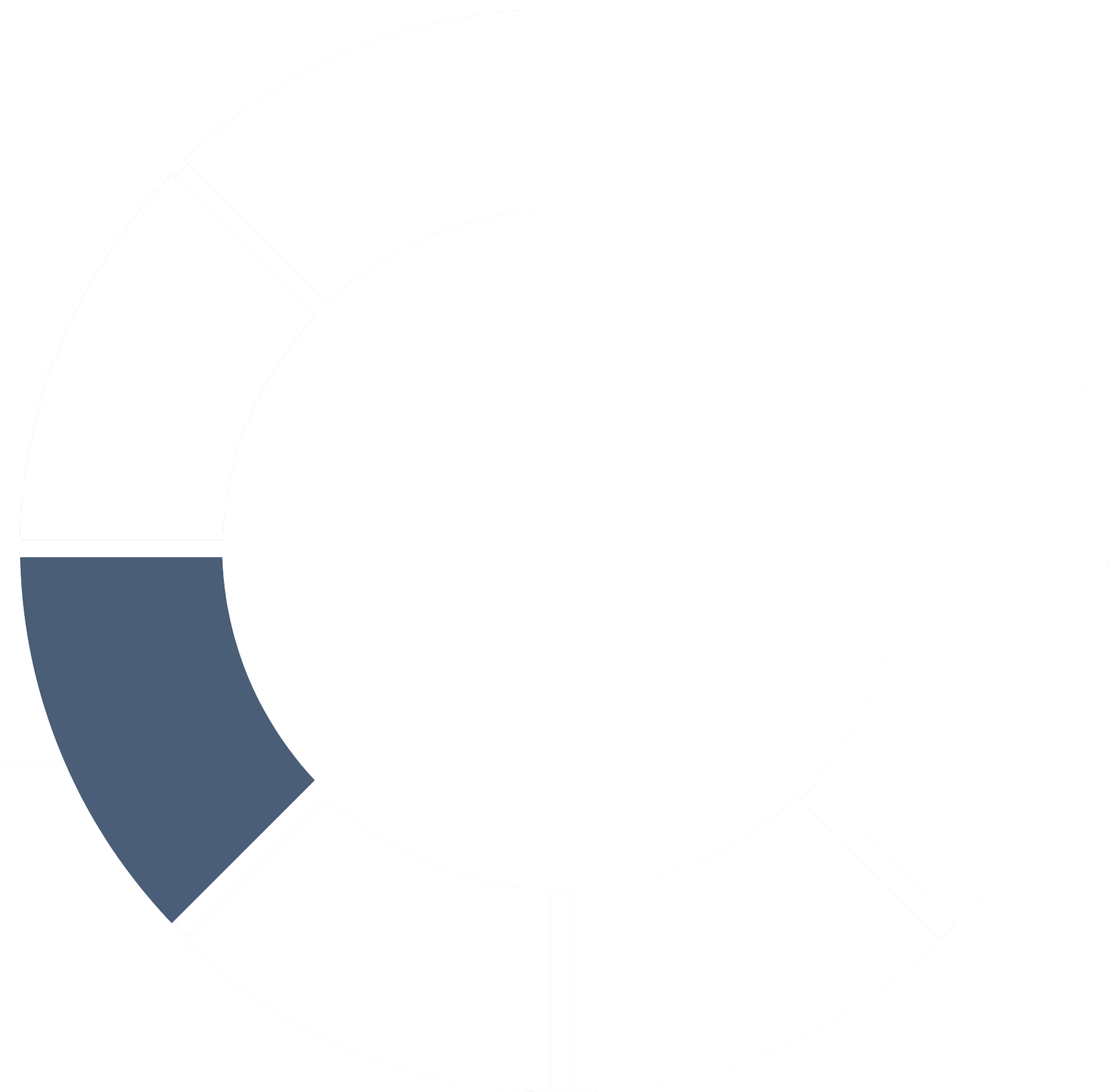
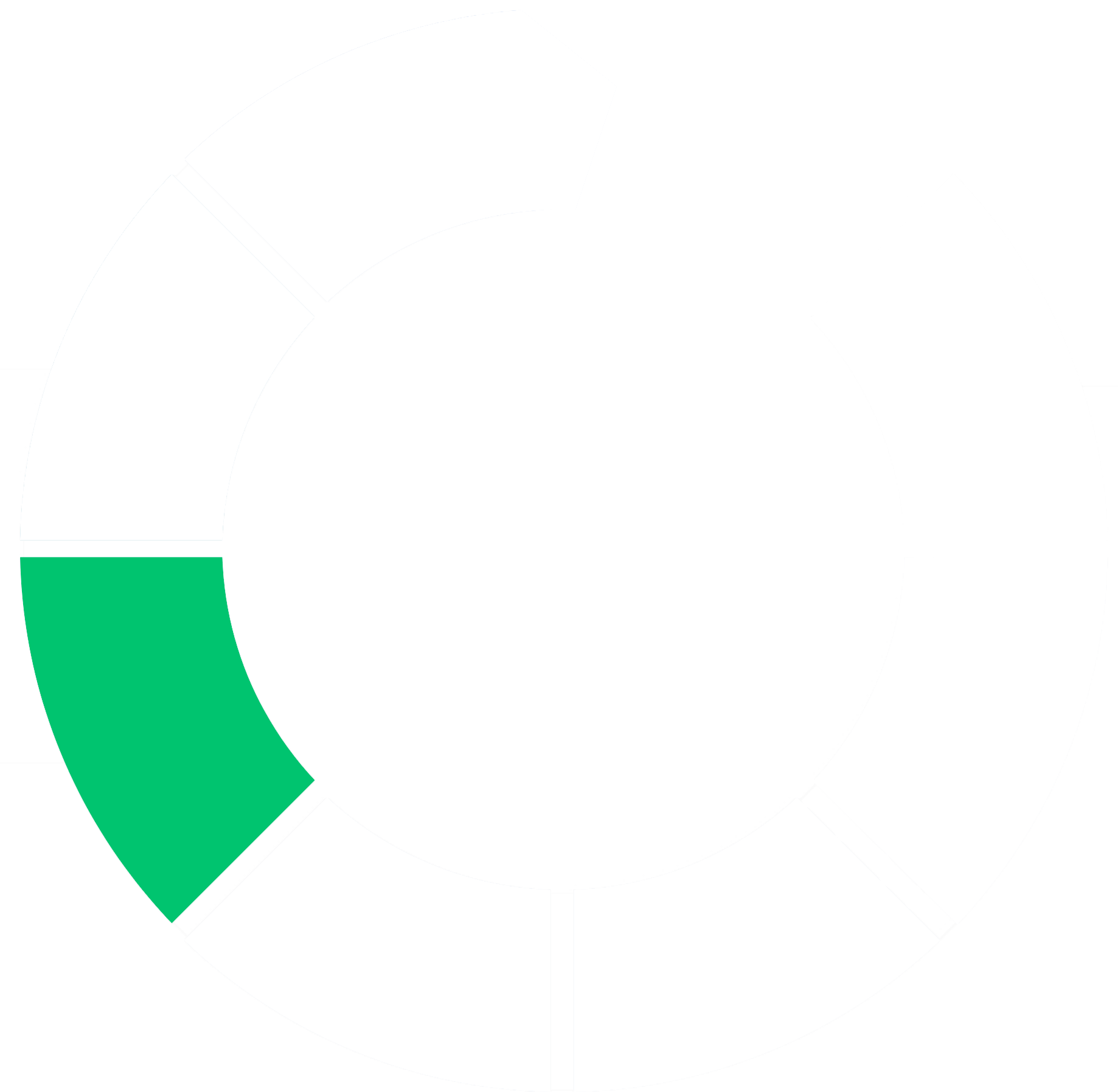
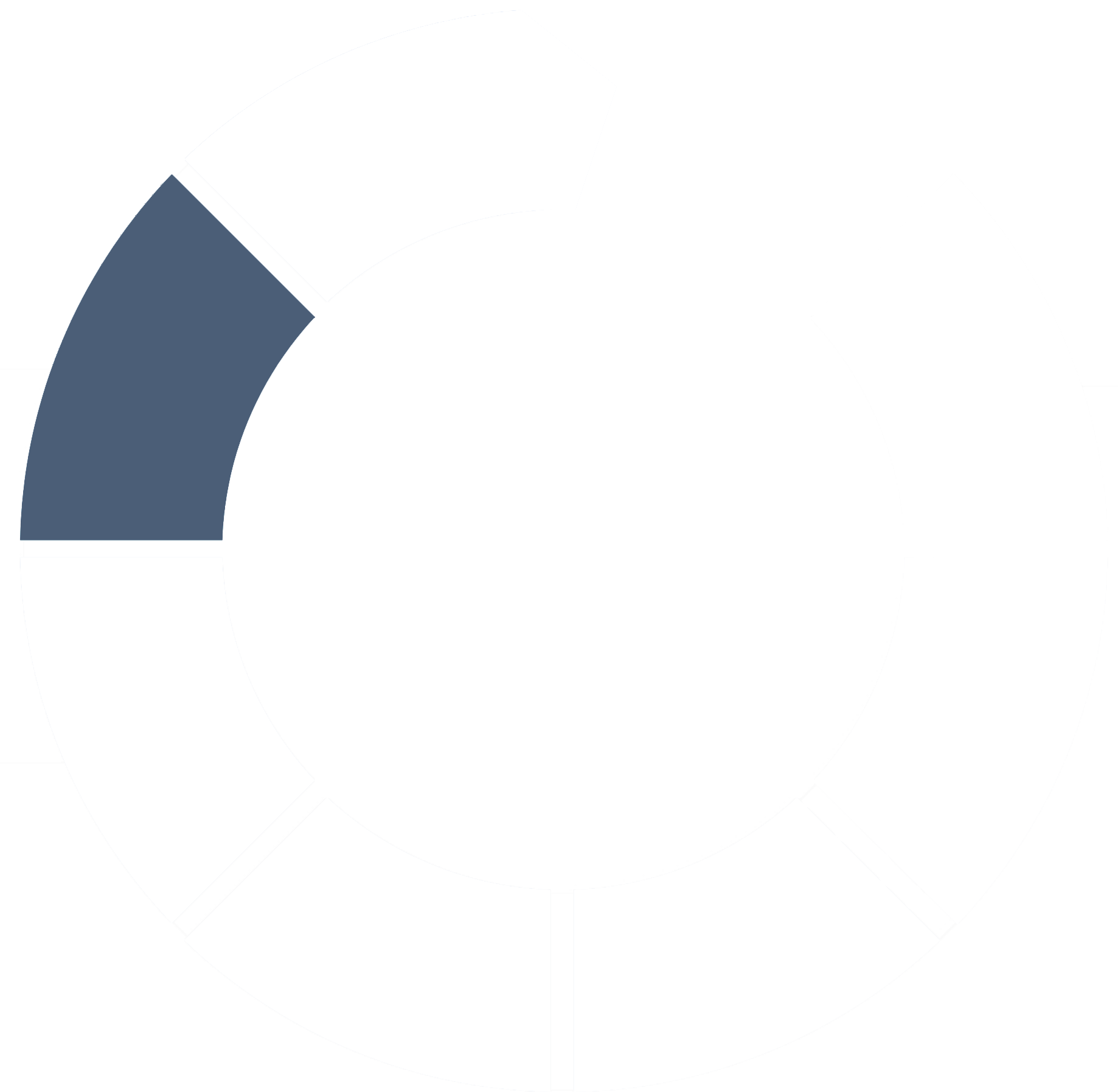
It’s critical to have a clear security framework so you can identify and implement the right controls to build the strongest security posture for your business.
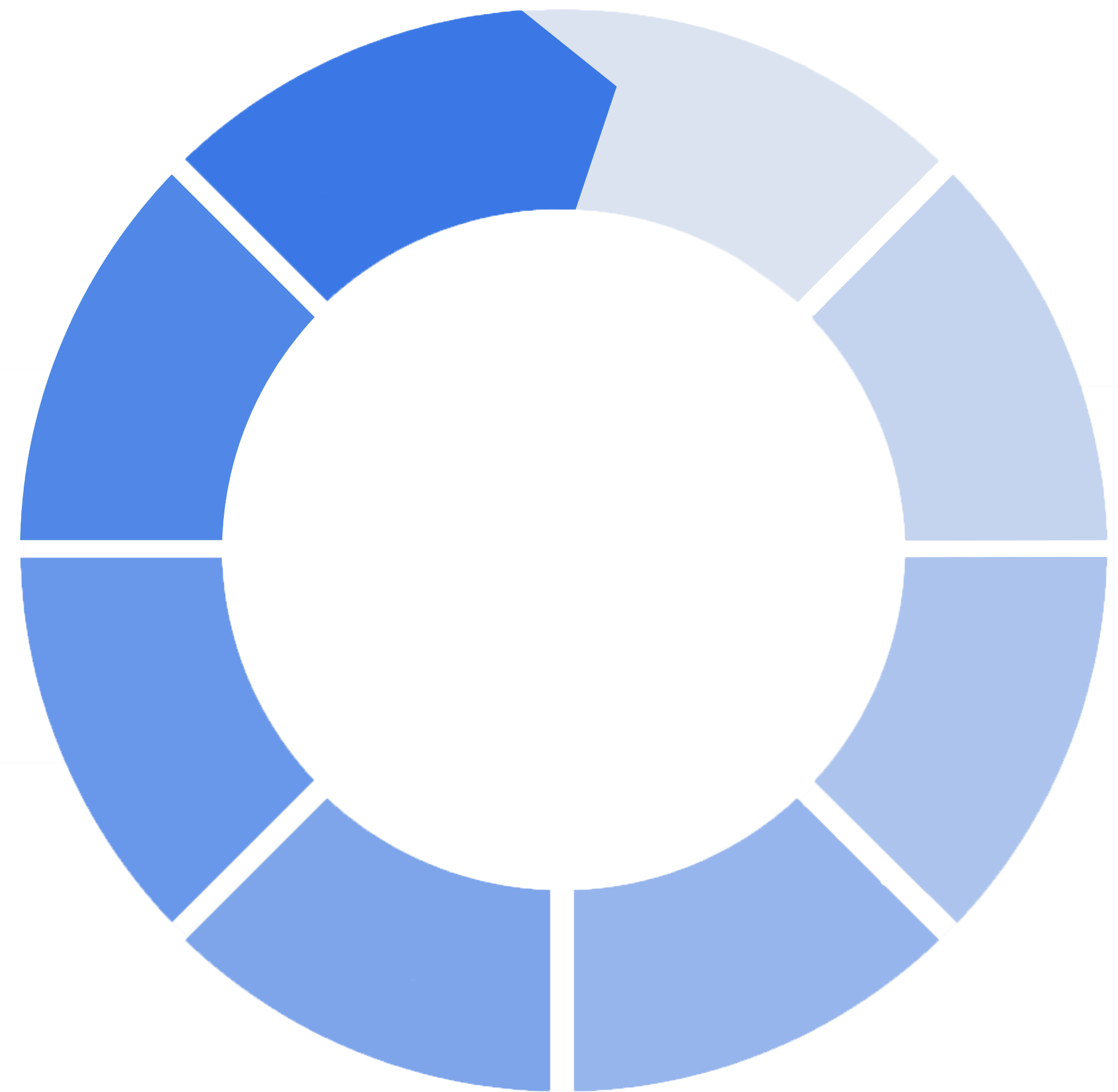
Nuspire’s Security in Action (SIA) framework is the foundation of everything we do with our clients. It includes measures we often see missing in security frameworks, such as customization aligned with specific client goals, existing technology and industry needs, as well as continuous improvement of a security program over time.
The SIA framework is based on your industry, technology, infrastructure, staff, expertise and other variables. It allows you to emphasize or de-emphasize certain framework elements depending on your organizational current state, goals and industry.
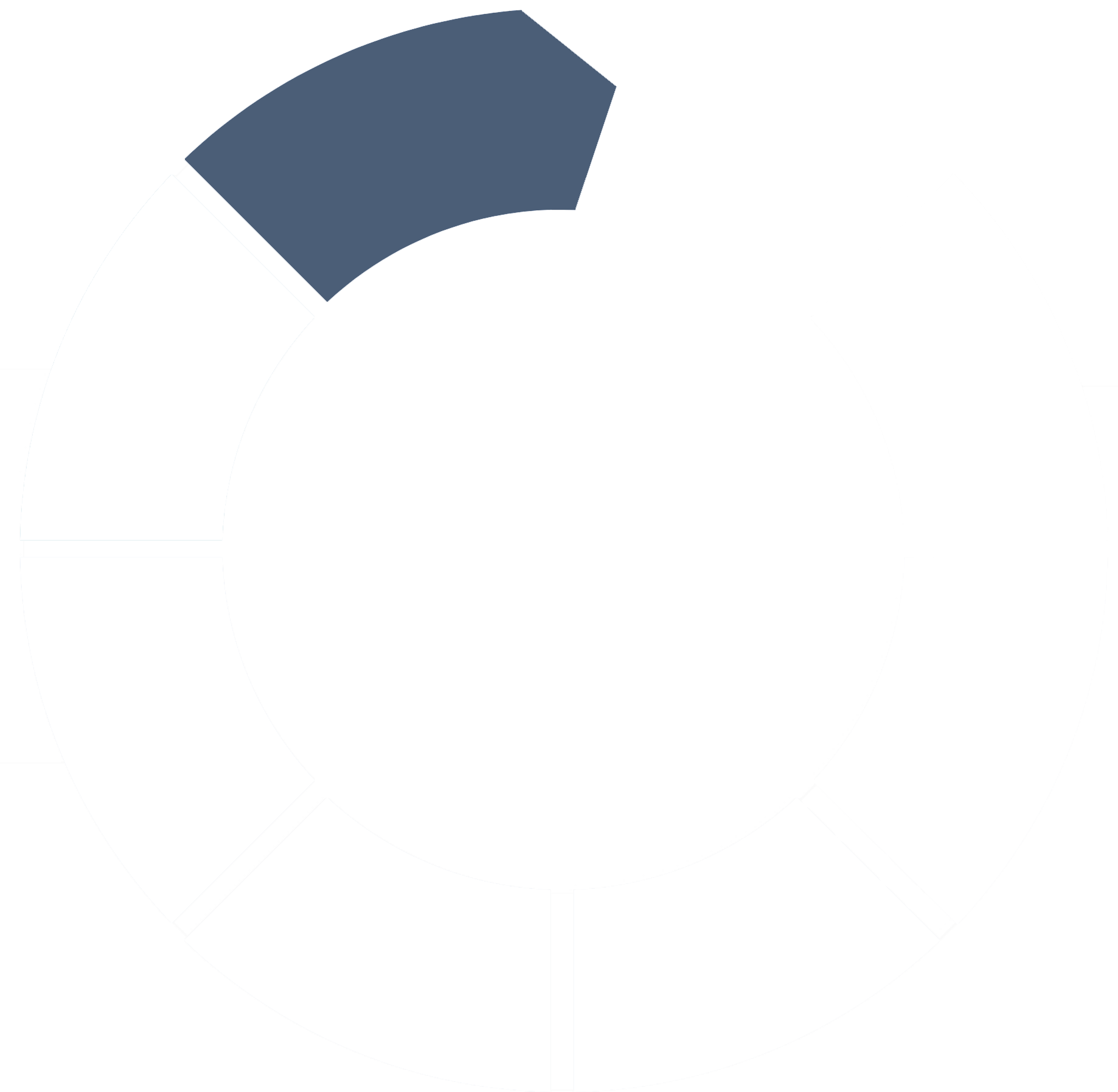
1. Discover
Thorough, complete discovery and onboarding may be the most important influence on outcomes. A consultative, collaborative process sets the stage for all that follows. Discovery is a great opportunity to be accurate and precise in capturing relevant business objectives, risk factors and security goals—and to clarify your threat landscape and implement the right controls and communications.
Additionally, the process:
- Sets the tone and expectations for the service provider.
- Helps you build a security program that combines what is known about your organization, such as goals and existing technology and services, with industry and cybersecurity intelligence.
- Builds trust in data from many sources to create a safer environment with appropriate security controls.
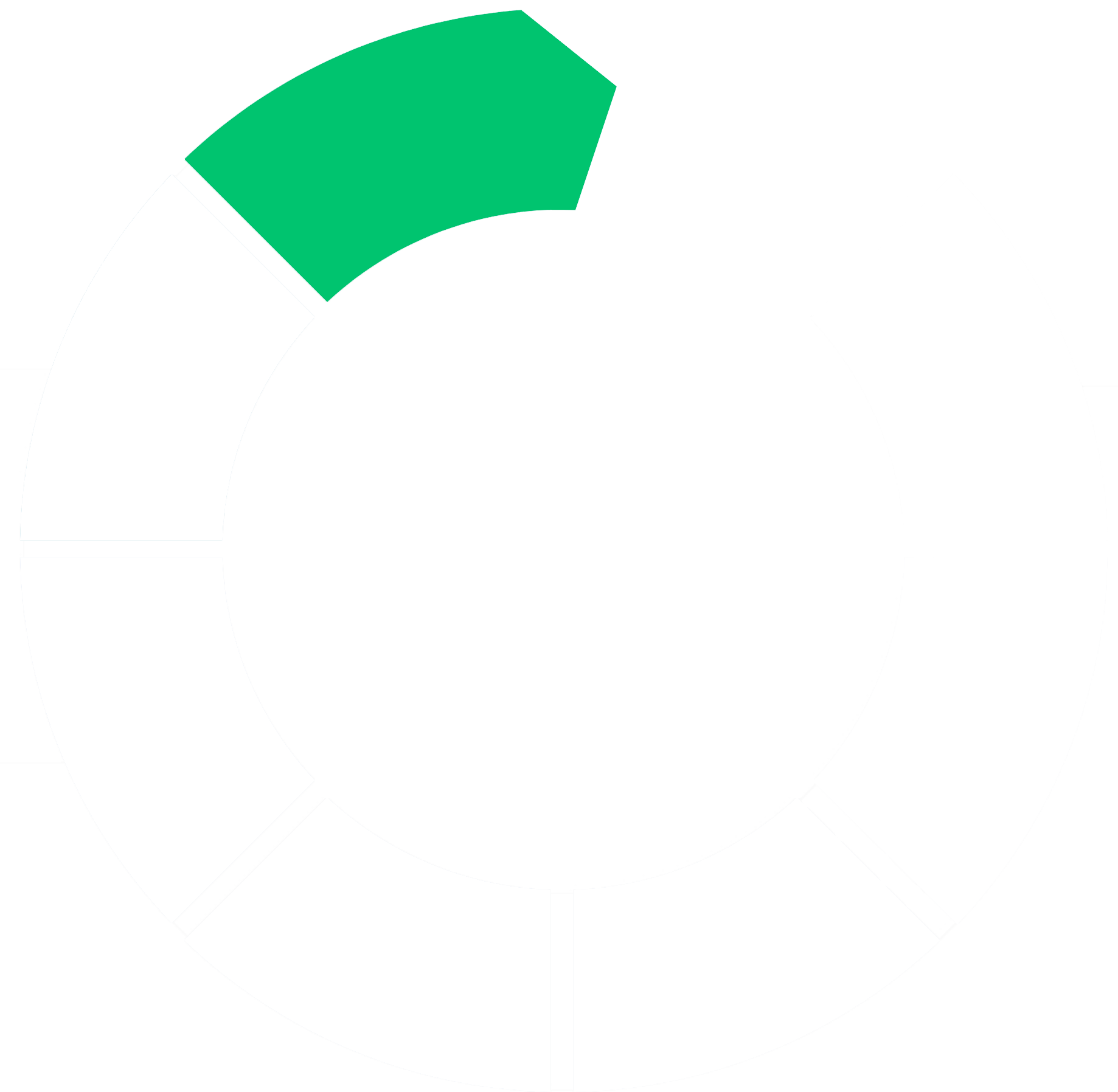
2. Focus
Apply Discovery findings to prioritize threats and mitigation efforts based on greatest risk—a direct way to reduce overall organizational risk and pinpoint where to optimize your valuable resources.
Additionally, the process:
- Create a roadmap prioritized by findings for technology and services.
- Receive recommendations from cybersecurity experts. View, keep tabs on and manage your roadmap (and ultimately your entire security program).

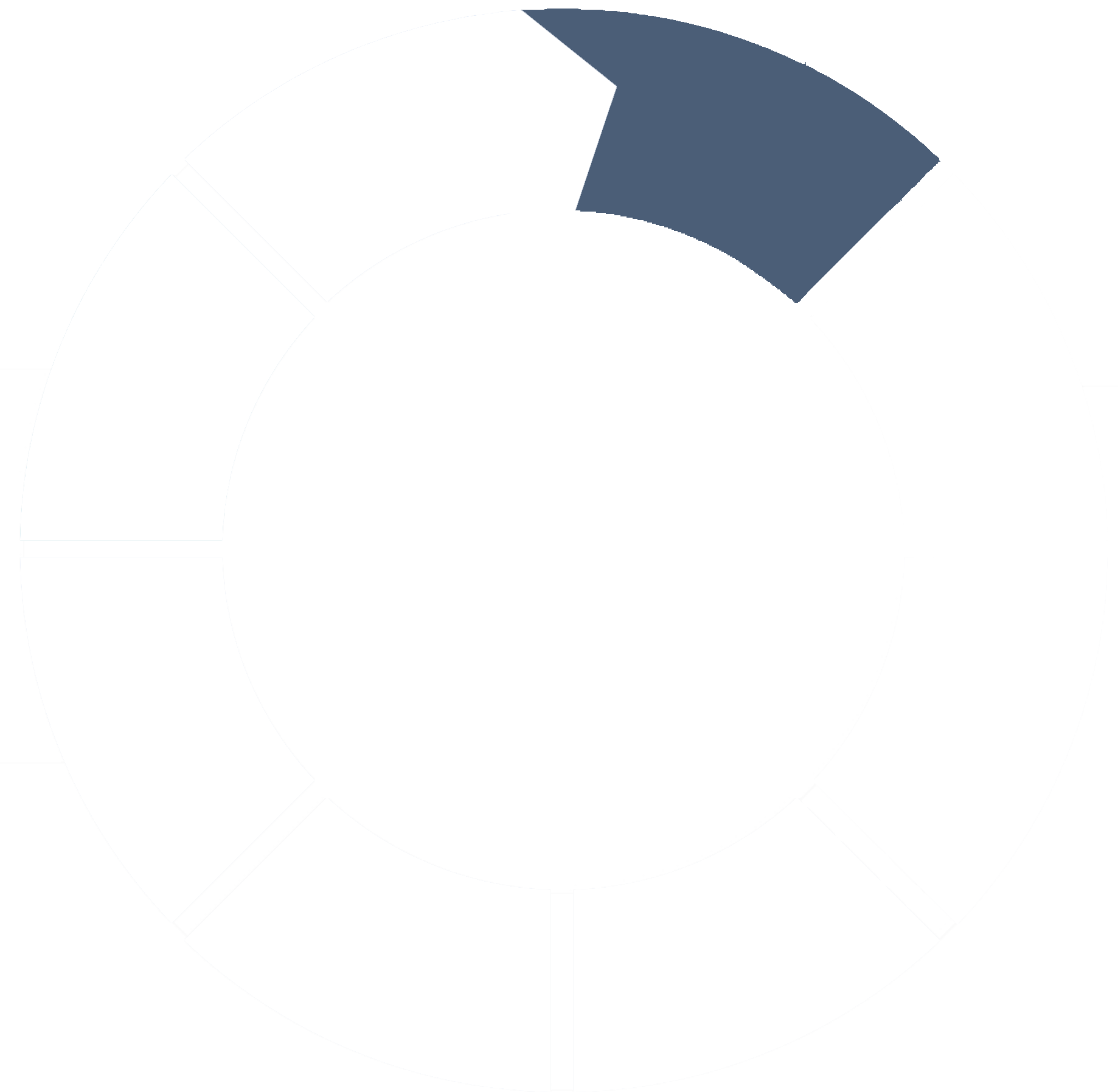
3. Prepare
Maximize threat visibility, close high-risk gaps, eliminate overlaps and/or add required security controls:
Additionally, the process:
- Collaborate on architecture and solution designs.
- Create a security plan in collaboration with a provider’s security implementation team (SIT), security operations center (SOC) and network operations center (NOC) teams to make sure you are on the same page with prioritization.
Customize your needed services and technology priorities.

4. Monitor / Manage
Monitor and proactively manage your IT environment 24x7x365 with the aid of MSSP resources such as SOCs and NOCs:
Additionally, the process:
- Eliminate swiveling among multiple screens to get as close as you can to operating with a single point of view.
- Acquire services that align to what you have already and where you need to be.
Keep track of your entire security program progress including tickets, potential threats, services and technology.

5. Notify
Communicate based on the alerts and processes set up during onboarding:
Additionally, the process:
- Reduce false positive alerts.
- Receive threat alerts and detailed information about what to do next.
Receive instructions for further actions if they are required.

6. Contain
Get the help you need to contain threats and mitigate potential damage:
Additionally, the process:
- Receive assistance from dedicated experts such as a provider’s SIT, SOC and NOC resources.
- Work with a certified security incident response team (SIRT) to expedite containment.
Minimize business disruption with automated response options.

7. Mitigate
Experience proactive response management:
Additionally, the process:
- Respond to threats 24x7x365.
- Remove threats using manual or automated methods.
Return to steady state as quickly as possible.
8. Maintain / Evolve
Assess and improve your security posture:
Additionally, the process:
- Access on-demand security reviews that give you real-time data, threat intelligence, recommendations and service performance information
- Make decisions based on metrics and ongoing threat modeling
- Add guided reviews for a live session with a security analyst, including customized recommendations
Adjust your security program and controls to keep up with the changing threat landscape and business/industry requirements.