Interactive Report Summary
Q2 2022 Threat Report
Nuspire Sees Dramatic Uptick in Q2 2022 Threat Activity
Q2 2022 saw a dramatic uptick in activity across all three of our tracked sectors: malware, botnets and exploits. Learn more about the biggest threats we saw, plus get a look into the manufacturing industry’s threat landscape in our latest report.
Top Findings at a Glance
Industry Spotlight: Manufacturing
Manufacturing continues to be a popular industry target, fending off attacks from LockBit Ransomware Gang and Dynamite Panda (APT18).
Some of the most popular tactics used by LockBit include phishing, purchasing stolen credentials and access to compromised organizations from other threat actors, as well as exploiting exposed vulnerabilities. Dynamite Panda is a nation-state sponsored APT group that performs espionage operations that include the theft of intellectual property.
Methodology
Hover over tiles to learn more
Q2 2022 in Review
April through June
Total Events
Unique Variants
Total Activity
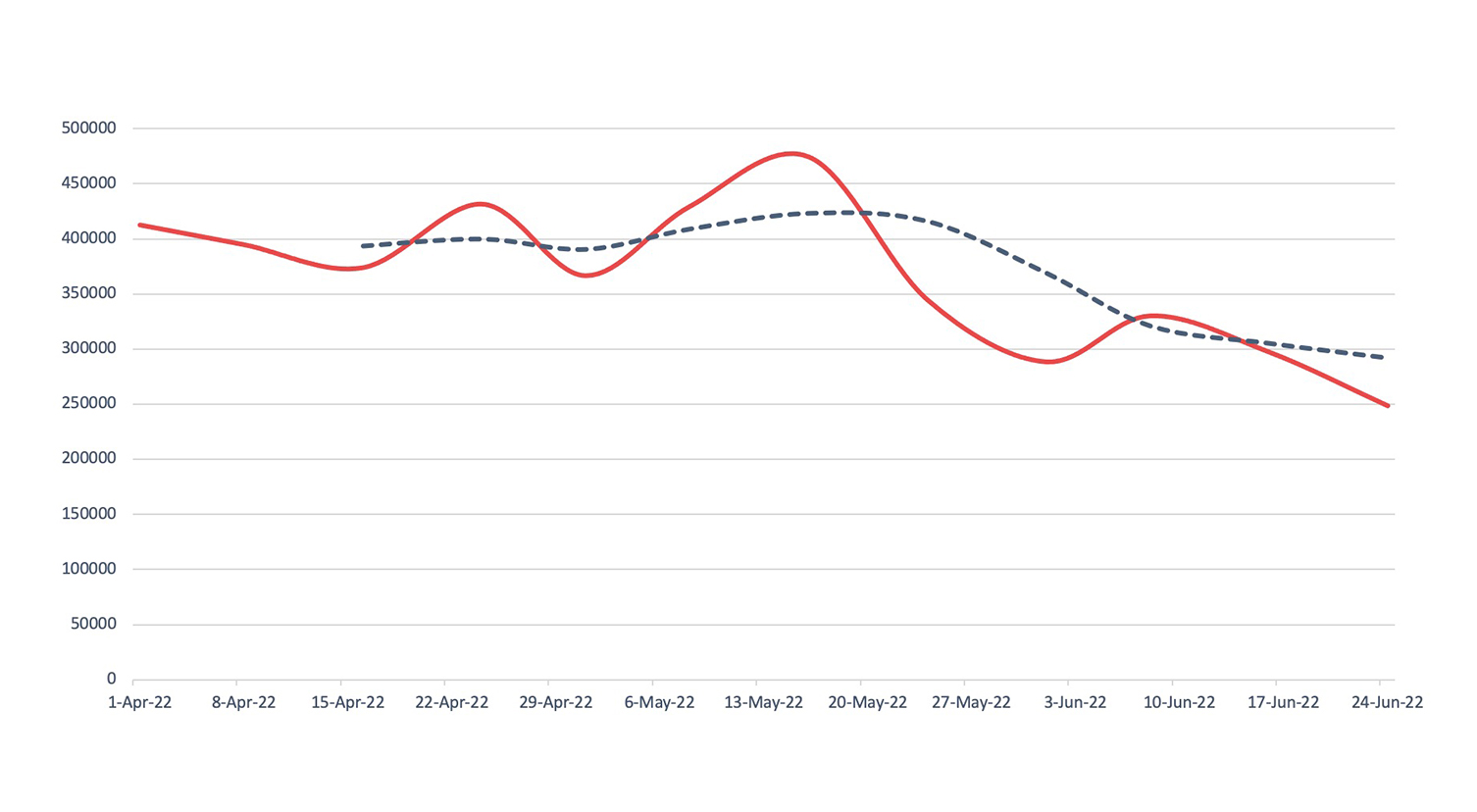
Malware
Detection, Q2 2022Across Nuspire managed and monitored devices, there was an increase of 28.1% in total malware activity compared to Q1 2022.
How to Combat
To strengthen your defenses against malware activity, you’ll need to adopt a multiprong approach including endpoint protection platforms and cyber awareness training.
Malware
With the rising popularity of cryptocurrency, crypto mining malware activity has increased. This quarter, CoinMiner malware took over as Nuspire’s top witnessed malware. This malware has a clear goal: to install itself on a machine, be as quiet as possible, leech resources from the victim machine and mine cryptocurrency.
Total Events
Unique Variants
Total Activity
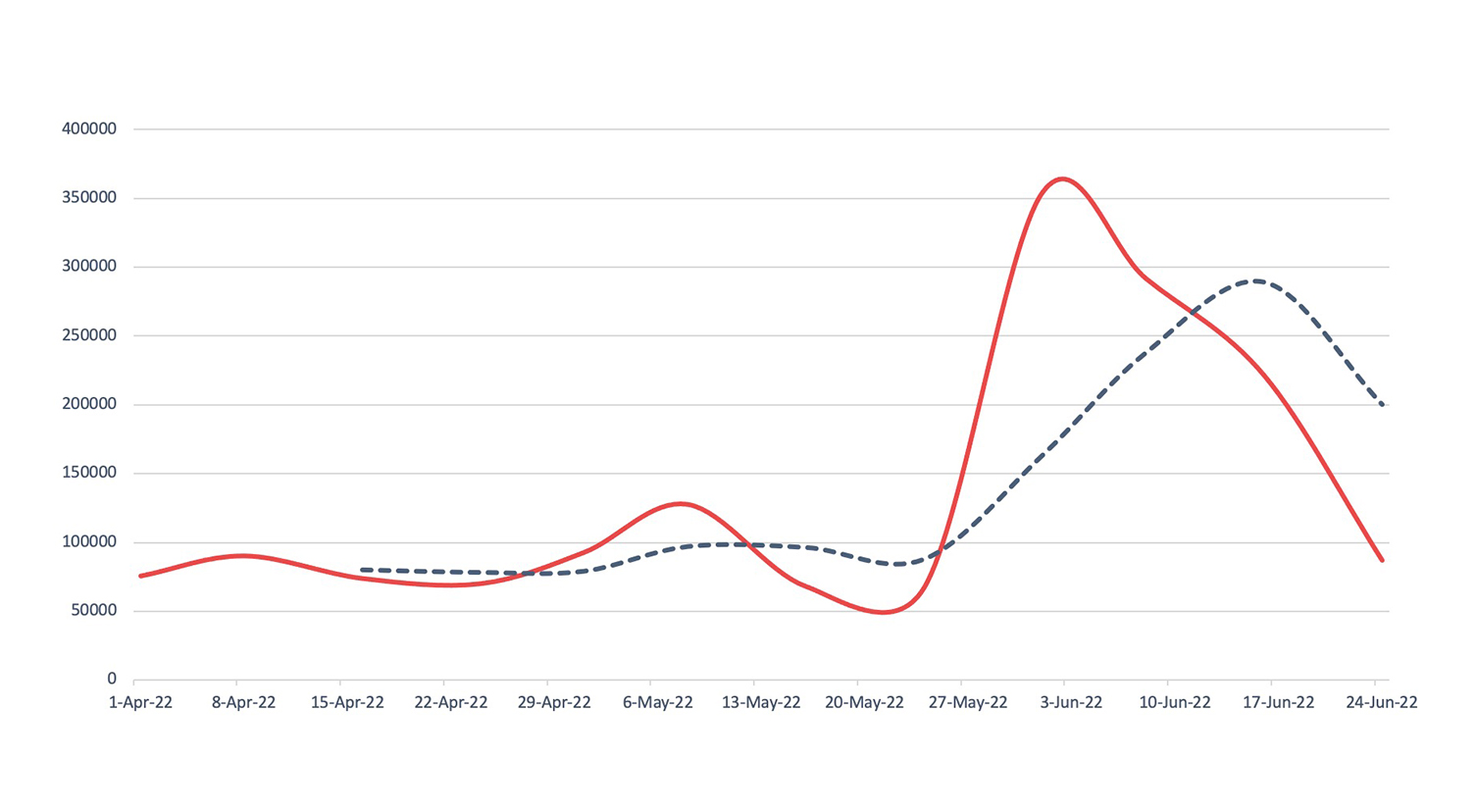
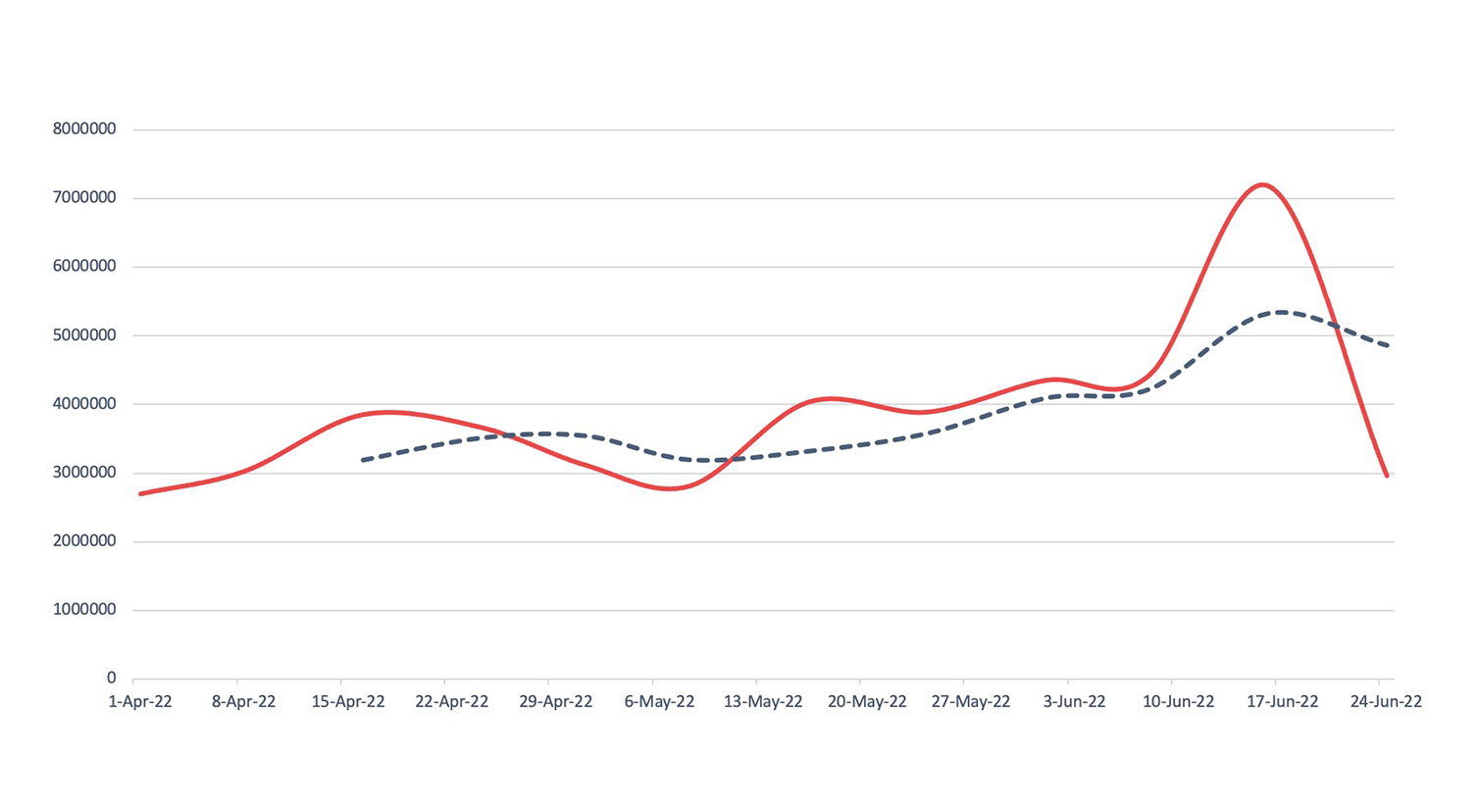
Botnets
Detection, Q2 2022Nuspire saw an increase of 100.14% in botnet activity.
How to Combat
Step up your efforts to stop botnet activity, which is usually detected post-infection. We recommend detecting malicious activity and quarantining devices to minimize botnet spread throughout the network.
Botnets
Torpig Mebroot surged toward the end of Q2. A banking trojan designed to scrape and collect credit card and payment information from infected devices, Torpic Mebroot is particularly difficult to detect and remove, as it infects the victim machine’s master boot record. The malware also provides backdoor access to threat actors to maintain connectivity with a device and allow additional malware to be installed.
Total Events
Unique Variants
Total Activity
Exploits
Detection, Q2 2022Exploit activity grew by a staggering 144.87% over Q1 2022 data.
How to Combat
Stop exploits before they do harm by patching systems and security monitoring to thwart attackers and decrease risk.
Exploits
DoublePulsar, an older exploit, re-emerged as a dominant threat in Q2. This is perhaps because variants of CoinMiner, a top-witnessed malware in Q2, leverage DoublePulsar to worm through a network and spread the infection.