Interactive Report Summary
Q1 2023 Cyber Threat Report
Top Findings at a Glance

Industry Spotlight: Technology
Technology companies often have a broad reach, access to data and a large user base, making them a prime target for financially focused threat actors or those interested in stealing intellectual data.
We’ve heard a lot about supply chain attacks, and for good reason. Often, a vendor doesn’t adhere to the same level of cyber discipline as the company it serves, and this can be an easy attack vector for adversaries. A recent example is 3CX, which endured a double supply chain attack, meaning its compromise was initiated from another software supply chain compromise.
Top technology threat actors include Lazarus Group, Kryptonite Panda, Comment Crew and UPS Team.
Methodology
How Nuspire produces its threat intelligence
Hover over tiles to learn more
January through March
Q1 2023 in Review
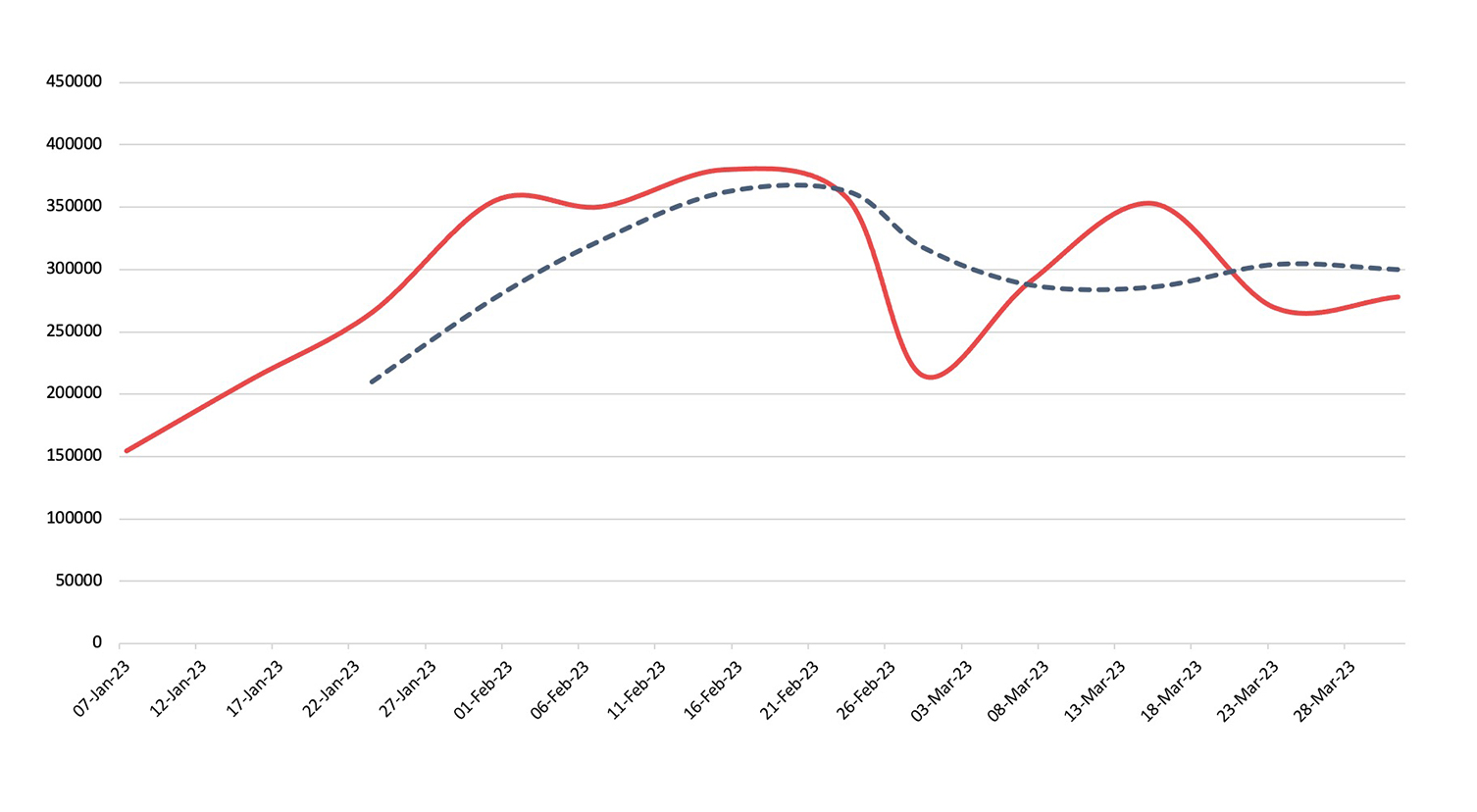
Malware
Detection, Q1 2023Across Nuspire-managed and monitored devices, there was an increase of 39.19% in total malware activity compared to Q4 2022.
How to Combat
To strengthen your defenses against malware activity, you’ll need to adopt a multiprong approach including endpoint protection platforms and cyber awareness training.
Malware
Throughout Q1, JavaScript variants continued to gain steam, with activity almost doubling in Q1. An increase in activity with this type of attack can likely be attributed to Microsoft’s default blocking of macros in Office files. In addition, we saw heightened activity of MS Excel variants, with a focus on using OneNote files to embed scripts given Microsoft’s blocking of macros in Word and Excel files.
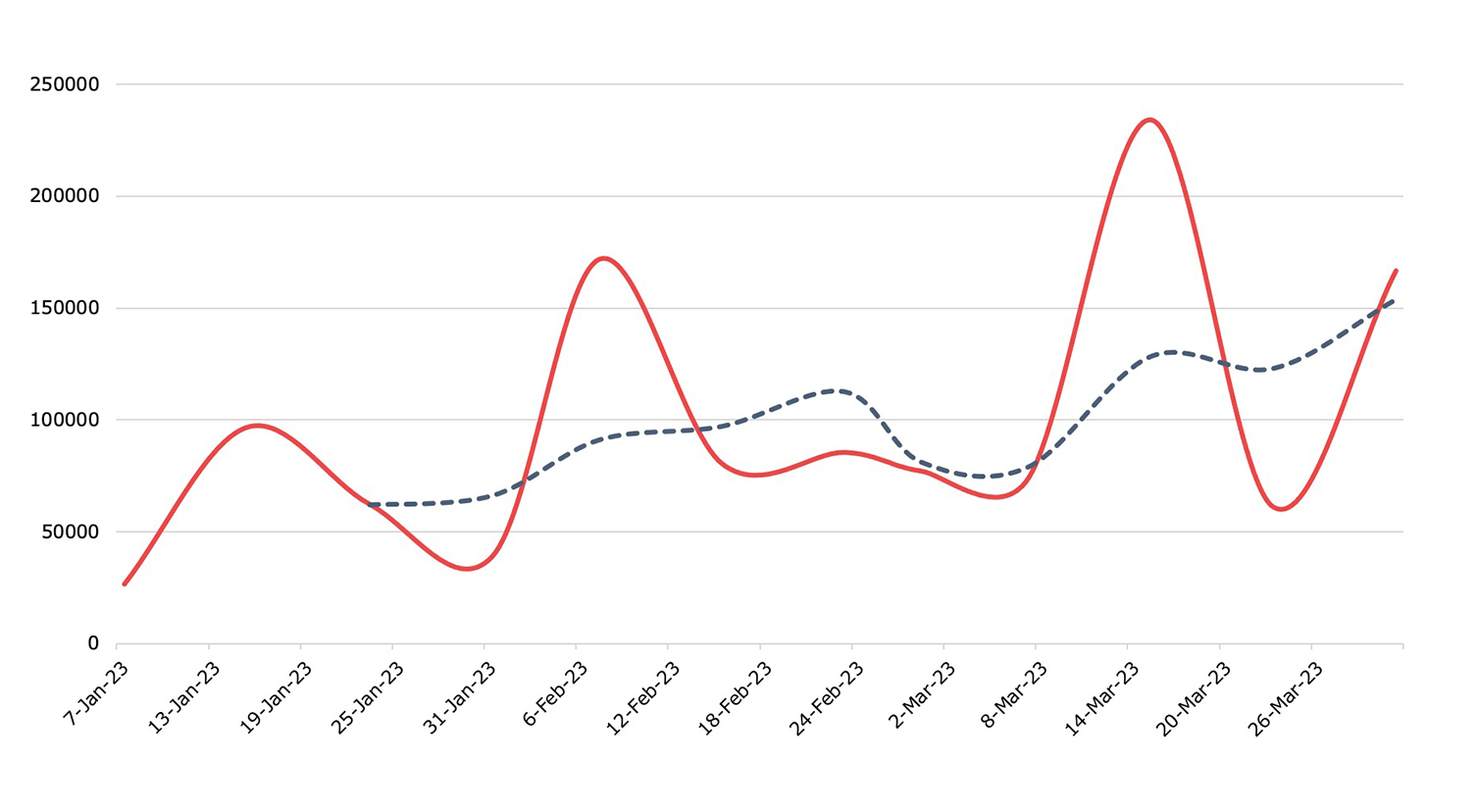
Botnets
Detection, Q1 2023Nuspire saw an increase of 58.23% in botnet activity.
How to Combat
Step up your efforts to stop botnet activity, which is usually detected post-infection. We recommend detecting malicious activity and quarantining devices to minimize botnet spread throughout the network.
Botnets
Two new botnets topped Nuspire’s list this quarter: NetSupport RAT and FatalRAT. Before March 2023, Nuspire had not observed any activity from the NetSupport RAT botnet. NetSupport is a legitimate tool for remote access; however, threat actors have abused the tool to:
- Conduct real-time monitoring of devices
- Take control of the device
- Capture video and screenshots
- Exfiltrate information
- Install additional payloads
FatalRAT is one of the primary payloads used by the Purple Fox threat actor group and is often retooled in an attempt to bypass security software.
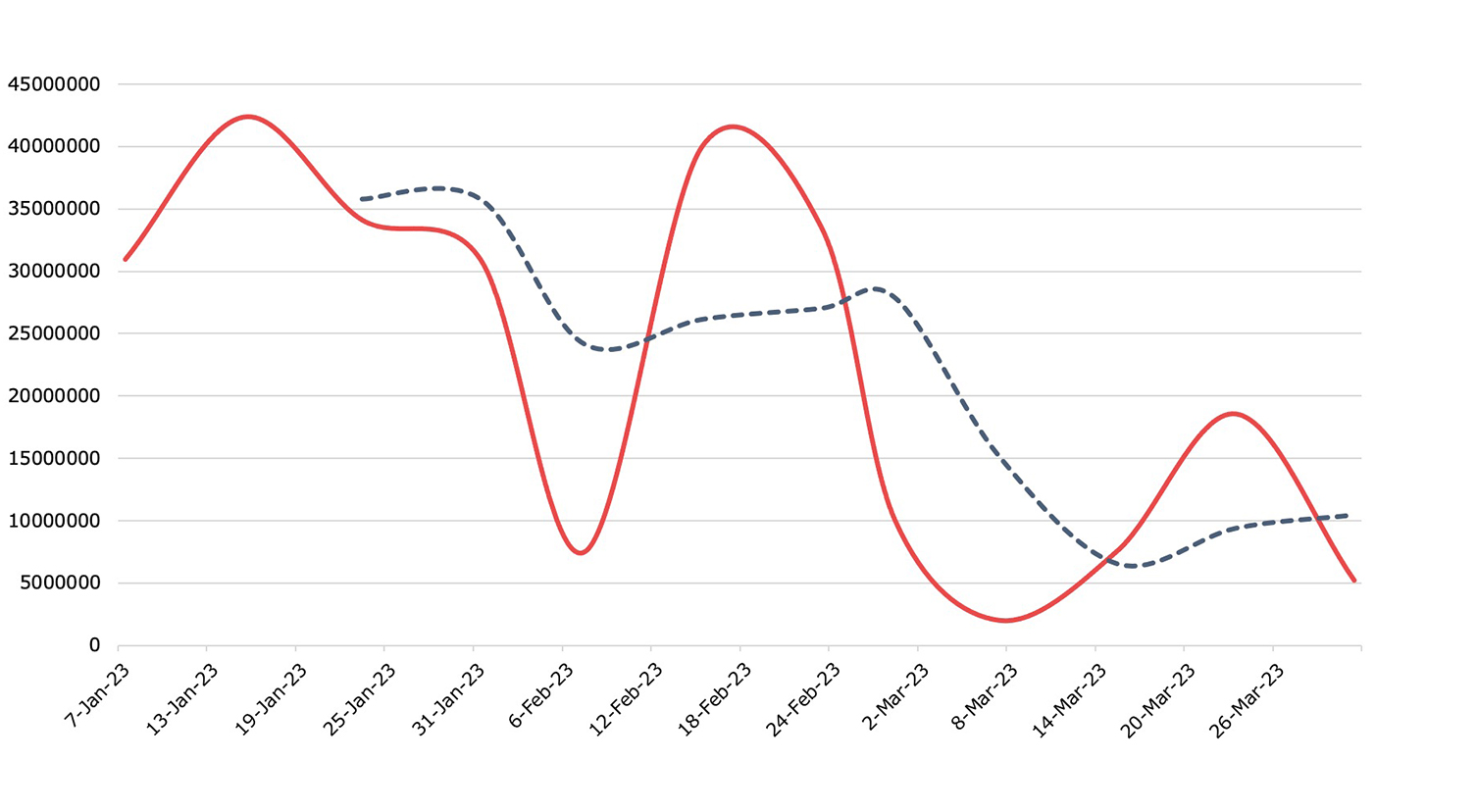
Exploits
Detection, Q1 2023Exploit activity exploded, growing 151.66%.
How to Combat
Stop exploits before they do harm by patching systems and security monitoring to thwart attackers and decrease risk.
Exploits
Brute forcing again dominated as the top exploit. In a distant second place was Apache Log4j, followed by Hikvision product command injections, which doubled from Q4 2022.