The 2020 U.S. Election and Phishing Attacks: Don’t Take the Bait
The fact that the 17th annual National Cybersecurity Awareness Month (NCSAM) falls just before the highly anticipated 2020 U.S. presidential election is symbiotic. This election and pandemic-driven work and learn from home models have created enormous opportunity for threat actors looking to inflict harm. And, they have wasted no time in doing so. Attackers are leveraging the election theme to wreak havoc, most preferring to utilize tried and true attack methods—like phishing—to gain foothold. And, an exorbitant amount of election communications from a plethora of sources have made it difficult for employees to identify an attack before it is too late. NCSAM provides a prime opportunity to give employees with the knowledge needed to identify an attack.
If you’ve read a recent news story about a cyberattack, there’s a good chance you discovered it began with a phishing attempt. Research suggests that 91% of all attacks begin with a phishing email.[1] Additionally, 32% of all successful breaches involve phishing.[2] It’s no secret that attackers need to have a good story, also known as a lure, like the upcoming presidential election to attract an end user to interact with their malicious payload.
Election-Themed Attacks Quickly Gaining Ground
More recently, attackers have been observed using voter registration as a lure. The Election Assistance Commission (EAC) released an alert stating phishers are spoofing [email protected] and utilizing EAC graphics. Attackers attempt at that point to direct users to a web form to collect information like date of birth, name, social security number and other personal identifiable information (PII).
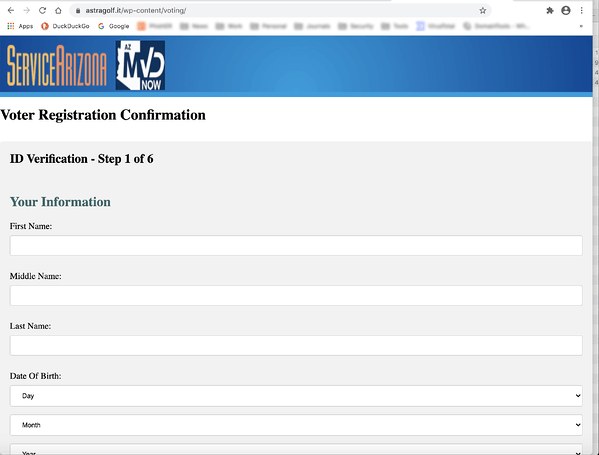
Source: KnowBe4
Additionally, Emotet phishing campaigns have been witnessed in the wild utilizing the election cycle as a lure. Emails with the subject line “Team Blue Take Action” include a malicious word document with embedded macros. Once those macros are enabled, they reach out to their command and control server to download the Emotet payload.
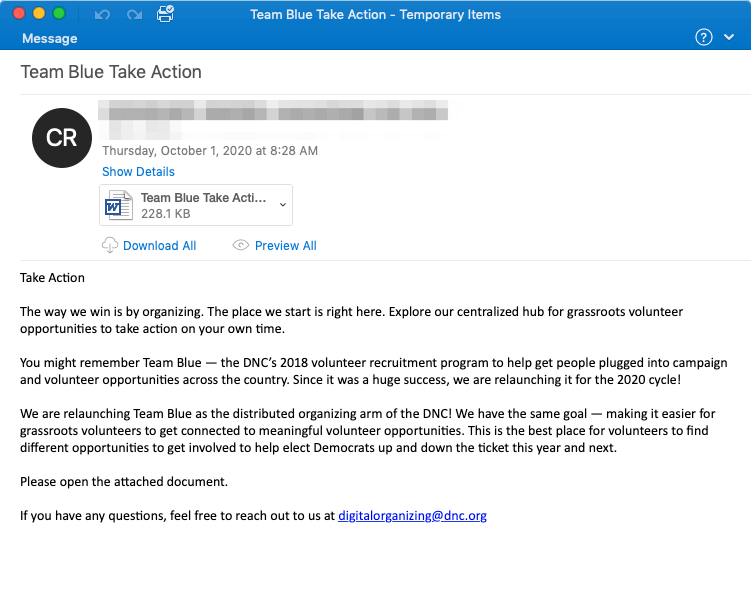
Source: ProofPoint
Phishing attacks are also taking advantage of typosquatting, the act of swapping out a character or replacing a phrase to catch users off guard. This happens when manually entering a website or it can be used to make a URL appear more legitimate at a glance in an email. Examples include swapping the letter ‘O’ for the number ‘0’ or replacing the phrase ‘for’ with the number ‘4’. This was a common tactic during the last midterm election used by attackers.
Phishing is nothing new. It is an effective tactic attackers continue to use because it is easy for them to deploy to massive amounts of people. It only takes the mistake of one employee to install a malicious payload that can result in the deployment of ransomware or a remote access trojan. Attackers know the weakest point of an organization is the human element and they will take any measure to abuse it.
How to Identify a Phishing Email
Most phishing emails create a sense of urgency and communicate negative consequences if you do not interact with it. Themes may include voter registration errors, changes in polling stations, new laws or guidelines, or related themes.
Educate your team on the following ways to identify a phishing email, so they don’t get hooked.
- Check the email address, is it coming from a generic email provider or from an official email address? Keep in mind though, email addresses can be spoofed.
- Hover over links in emails and ensure they are going to take you to the website you expect. Be vigilant for typosquatting.
- Verify grammar, spelling, sentence structure. If it seems off, it likely is.
- Is the email addressed to a generic person, or to you specifically? A lot of phishing emails are very generic.
- Inspect suspicious emails on a PC vs. mobile device as it is harder to spot errors on a mobile device.
- Do not enable macros on any document or spreadsheet you’re not expecting. This can download malware.
- Contact your administrators or security team for advice if you’re not sure. It is better to ask than execute a malicious file.
As we march closer to election day on November 3rd, the number of phishing campaigns will continue to increase. Ensure your teams are cyber aware and have the information needed to protect themselves, and your company’s data, from cyberattacks.

