CISA Releases Advisory Regarding Enterprise VPN Security
CISA has released an advisory regarding Enterprise VPN security with regards to organizations that may use VPNs to support work from home during the impacts of Coronavirus Disease 2019 (COVID-19).
The advisory reminds that VPNs are a target for malicious actors and publicly known vulnerabilities are actively exploited. Because VPNs typically are up 24/7, organizations are less likely to update them due to the associated downtime. Along with targeting VPNs, malicious actors may increase phishing attempts specifically targeting teleworkers in an attempt to steal credentials.
Phishing emails surrounding the COVID-19 can take different forms within your inbox, including:
- CDC Alerts. Hackers are sending emails looking as if they are from the U.S. Centers for Disease Control. These emails may hint at the availability of a cure or vaccine, claim to be from a charitable organization, or simply offering updated information on the virus.
- Workplace policy emails. Hackers are also targeting employee emails referencing updated company policies due to COVID-19. These could be regarding working remotely, implementing policies to protect employees, or paid sick leave updates.
- Health advice emails. Cybercriminals are using the threat of the coronavirus to send safety and medical precautions that can protect you against the virus.
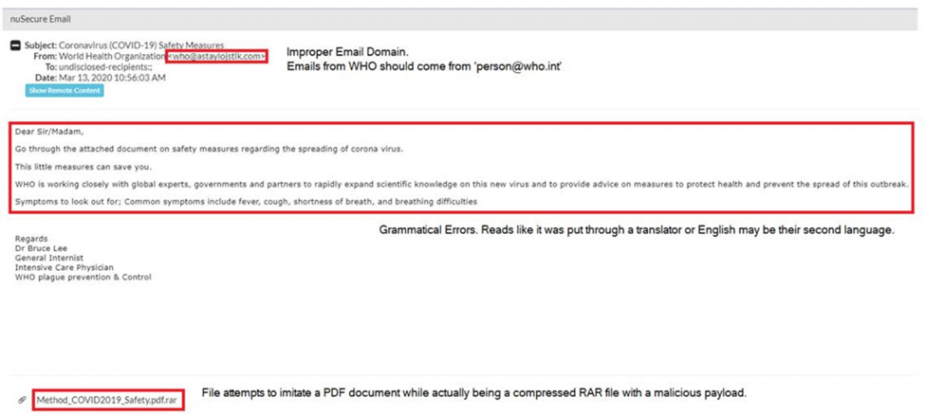
In a recent email detected by our own SAT team, a cybercriminal used this particular tactic to try and infiltrate a client’s network, claiming to be from a legitimate organization offering information regarding the coronavirus.
To learn more about phishing and how to protect your organization, click here.
How to prevent
Multifactor authentication (MFA), which cross-verifies users via two different forms of identification prior to login, is a good best practice to protect against phishing attacks. If MFA is not an option for your organization, creating strong, unique user passwords should be required.
Another consideration is that organization’s VPNs may only support a limited amount of VPN connections, creating a bottleneck for teleworkers effecting business operations. Organizations should ensure their VPN solutions are updated during this critical period and they should alert employees to expect an increased number of phishing attempts.
How to tell if your VPN is updated:
- The first step to ensuring your VPN is updated is to look up which version your product is on. If you do not know which product or version your VPN is, this could be done by asking one of your system administrators. Most products will inform you if there is an update or firmware update available, however it would be beneficial to confirm with your product vendor to see if there are any new updates available. This will ensure the VPN has the most up to date version.
- Additionally, you can also check to see if there are any specific vulnerabilities by going to https://cve.mitre.org/, then selecting “Search CVE List” in the top black banner. Once that is pulled up, you can search for a specific vendor product and find all known vulnerabilities. Inside of the CVE, if known, the site provides references to the vendor’s advisories which usually has patching/mitigation information.
IT Staff should test VPN connection limitations to allow organizations to plan for prioritization of VPN user usage and rate limiting if required.
*As a reference, CISA has a page dedicated for Social Engineering and Phishing Attack awareness that can be found here: https://www.us-cert.gov/ncas/tips/ST04-014