CISO-centric Security Trends and Lessons from 2021
With 2021 winding down, it’s a good time for security practitioners to not only reflect on what we learned, but also look ahead to 2022 and understand what threats could be on the horizon – and plan accordingly.
That’s why Nuspire invited Jess Burn, Senior Analyst from Forrester, to join us as a guest speaker on a recent webinar to share research and findings around 2021’s top threats and trends, as well as predictions for 2022. Jess was joined by two of Nuspire’s leaders – CSO J.R. Cunningham and CPO/CMO Michelle Bank – to provide additional color on what they’re seeing from an MSSP perspective.
Read Forrester’s report on top recommendations for your security program
Top 2021 Trends, 2022 Predications & Recommendations
Insider Risk
Insider risk was a big issue in 2021 given the sweeping shifts we saw in the workforce resulting from the COVID-19 pandemic. From layoffs and hiring freezes to work from home environments, the risk of malicious activity resulting from job losses or employees incorrectly using home networks rose significantly.
“The security team supported this big move and other accelerated moves to the cloud, often working long hours triaging this new, unstable attack surface,” said Jess during the webinar. “CISOs were writing net new policy about what devices to share, or not share, connecting via VPN, and even disabling or removing virtual assistants like Alexa from home office spaces.”
2022 Predictions
According to Jess’ presentation, this spurred employers to begin installing “tattleware” to monitor employees’ activities at home. For 2022, Forrester predicts tattleware will degrade the employee experience by 5% and increase insider threats. They also anticipate security brain drain will set in as one in 10 security professionals will leave the industry.
Recommendation
“There’s a number of recommendations to mitigate the problem of security attrition but, for all employees, we recommend finding the right balance between security and privacy if you feel the need to use monitoring software,” Jess said.
During the webinar, Jess recommended that in the short term, it’s important to empower your workforce to handle data the right way and understand the risks of remote work. In the long term, she said to involve functions like internal audit, risk, privacy and HR to develop a well-defined and repeatable process for responding to suspicious activity and investigations.
Third Party Risk
Forrester listed identity theft and account takeovers as top threats in 2021 – especially in the supply chain arena. In fact, according to its 2021 Business Technographics data, they saw that 55% of security practitioners reported that their business experienced an incident or breach involving supply chain or third-party providers in the last 12 months.
“Of all the incidents Nuspire responded to, 80% had a third party involved,” said J.R. “In half of those incidents, it was a fourth party providing services to third party that was the source of the original concern.”
2022 Predictions
In 2022, Forrester predicts this threat to get worse, with 60% of security incidents resulting from third parties.
“This will lead both firms and their insurance carriers to transfer risk associated with third parties with low security maturity back on to those third parties in the form of cyber insurance policies embedded into annual contracts,” said Jess on the webinar. “So, if one of your partners can’t prove that they meet your minimum security requirements, they will need to assume the risk of an intruder jumping from their poorly secured environment over to yours.”
Because of this, Forrester anticipates one-fifth of firms will embed cyber insurance policies in third-party contracts.
Recommendation
“Our recommendation is to get serious about third-party risk management,” Jess said on the webinar.
In the short term, Jess discussed inventorying all third-party relationships and prioritizing ongoing assessments of those that access or connect directly to your network, transmit, store or process data considered identifiable or have access to sensitive data.
In the long term, it’s about conducting specific risk management activities throughout the relationship.
“Notably, each state of relationship introduces new types of risk to organization,” said Jess on the webinar. “If you only do assessment at beginning, you’ll fail to identify changes to that company’s risk profile.”
Ransomware
There’s no question that in 2021, ransomware was the biggest concern among security practitioners, with 90% who responded to an ad hoc Forrester survey saying they’re worried about the threat. The problem is, there’s no clear consensus on the best tools to defend against ransomware, with responses ranging from doing backups daily to EDR to cyber insurance.
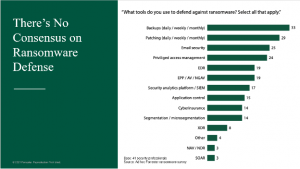
“The variety of different defensive strategies we see speaks to confusion in the market around where security practitioners invest when it comes to prevention versus detection and response,” said J.R. “Questions arise around whether security pros leverage a peanut butter approach and invest equally in these measures, or focus on a few of these measures where they’ll allocate the majority of their resources.”
“As an MSSP, we know we can’t be everything to everyone, so we’re working closely with our clients to understand how they define these areas and services and where we can provide the most value and support,” said Michelle. “For example, EDR. Last year was all about securing the endpoint and organizations now need help managing the EDR technology they invested in.”
How CISOs spend their days
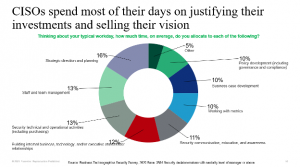
When you look at how CISOs spend their day, only a small amount is focused on technical or operational needs. What they’re actually doing is building cross-functional relationships, managing their teams, developing business cases and strategizing, which requires a lot of human interaction.
“It’s interesting looking through this – this is what it looks like when nothing bad happens,” said J.R. “The goal is to shrink these sections down so that as new threats emerge, we can respond without letting other things fall by the wayside.”
Michelle added, “We’ve refined our roadmap to align with how CISOs spend their days. It’s really about understanding what the end user is doing during their day, and how we solve their biggest problems to make their lives easier. It’s about the tools we need to provide that help CISOs build a business case to get more money from their management and invest in a better security program.”
Cyber insurance
According to data from the University of Virginia, cyber insurance has been the biggest security investment. In fact, in 2016, fewer than 50% of organizations had coverage, while today, that number has risen to 79%. That also means that the loss ratio for cyber insurance has risen. In 2019, it was 44.8% and grew to 67.8% in just one year.
“This looks like a massive transfer of risk from organizations at all maturity levels to carriers who had no idea what they were getting into when they started offering cyber insurance coverage,” said Jess during the webinar. “And this is 2020 data – 2021 is going to be next level.”
J.R. added, “Insurance is fundamentally changing how security programs are designed. We’re seeing a lot more involvement by insurance carriers to ensure a company’s cybersecurity program is doing what it’s supposed to be doing before they’ll write coverage.”
Something J.R. cautioned is that he’s seeing insurance policies that institute a waiting period before the policy kicks in. For example, if your company is the victim of ransomware, the insurance policy may not activate until 24 hours after the incident began.
Insurance is no longer the “catchall” option
“Cyber insurance is not cyber security – it should be thought of as insurance against the unforeseen – a novel attack situation you couldn’t possibly have prepared for,” said Jess in her presentation. “It’s not a replacement for a mature security program and certainly not coverage against the basic blocking and tackling needed to eliminate common paths of entry for attackers.”
So, what to do? In the webinar, Jess recommends focusing on two areas (although there are more):
- Justify security investments based on maturity. By linking increases in maturity to benefits like ransomware readiness and reduced or flat cyber insurance premiums will help the board and senior executives to make decisions with the mitigation of all those risks in mind.
- Conduct realistic, detailed tabletop exercises. Encourage executive involvement and understand where ecosystem players like your insurance carrier and outside counsel fit in before a major incident.
Communicating the importance of improving your cybersecurity program’s maturity is a key component of getting buy-in from senior management on budget needs. Plus, security maturity and security posture now tie directly to cyber insurance premiums since they’re an indicator of how susceptible your organization is to an attack.
“Back in early 2000’s to early 2010’s, we stopped talking about what bad guys were doing and focused only on controls and checks/balances,” said J.R. “Now we are acutely aware that we need to constantly assess maturity and make adjustments and investments to ensure my organization has what it takes to stay safe.
Communication and Collaboration
“I hope that you’ll consider the trends I went over with you and my recommendations for linking budget to maturity along with maturing your IR program as you begin planning for 2022,” said Jess in her presentation. “What we’re suggesting here does require a good amount of executive and business unit communication as well as collaboration with IT groups and, for some of the recommendations, significant change management.”
To watch the full discussion, click here.