Interactive Report Summary
Q3 2021 Threat Report
Top Findings at a Glance

While ransomware saw an 18.55% decrease in Q3, we expect to see it surge again during the holiday season.
Nuspire team witnessed dangerous vulnerabilities targeting Microsoft Exchange servers: ProxyShell and ProxyLogon.
Methodology
Hover over tiles to learn more
Q3 2021 in Review
July through September
Total Events
Unique Variants
Total Activity
Malware
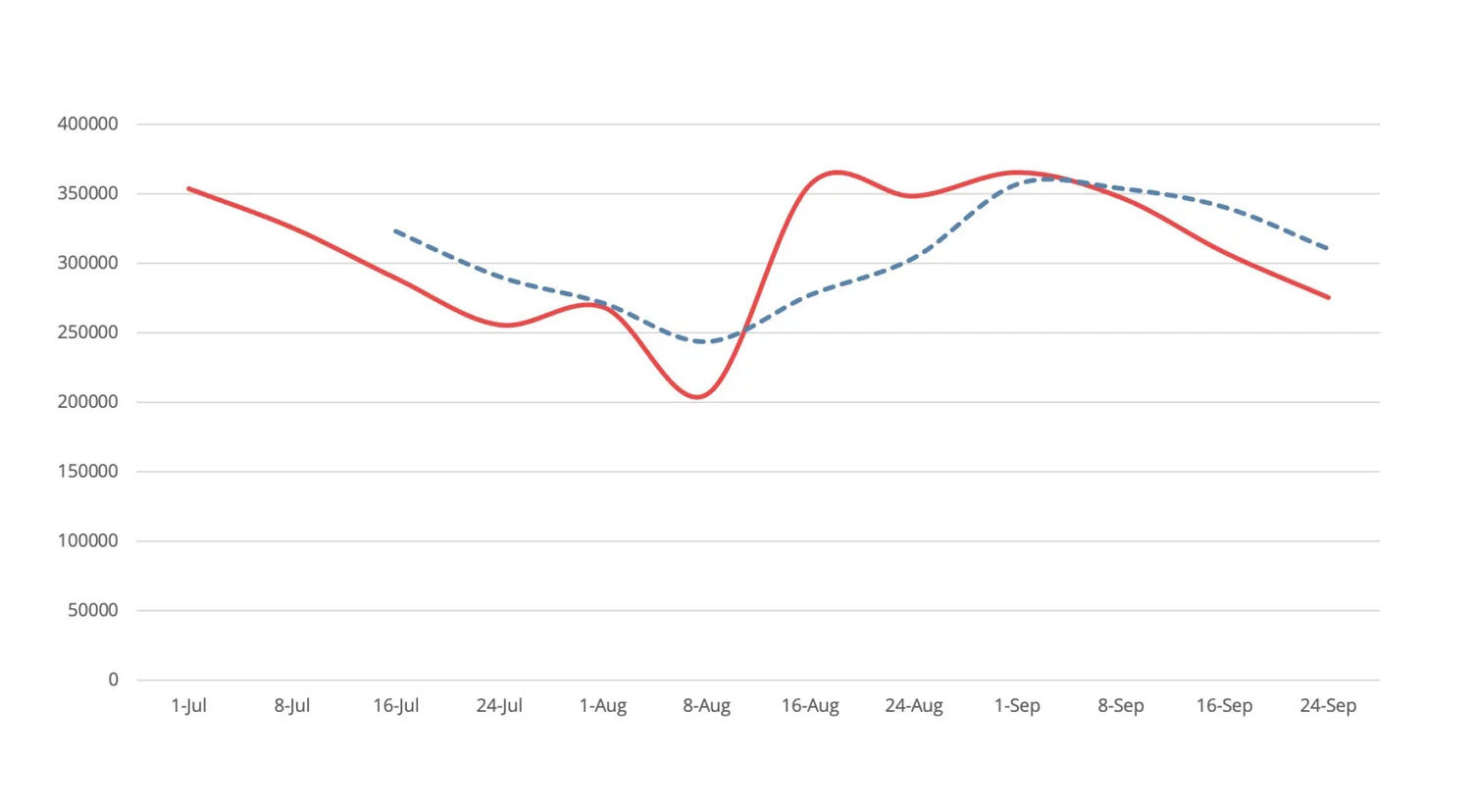
Detection, Q3 2021Across Nuspire managed and monitored devices, there was a decrease in total malware activity compared to Q2.
How to Combat
To strengthen your defenses against malware activity, you’ll need to adopt a multiprong approach including endpoint protection platforms and cyber awareness training.
Malware
As previously witnessed, VBA Agents continue to dominate malware activity, as these are commonly deployed in phishing malspam campaigns and act as an initial loader for other malware families.
Total Events
Unique Variants
Total Activity
Botnets
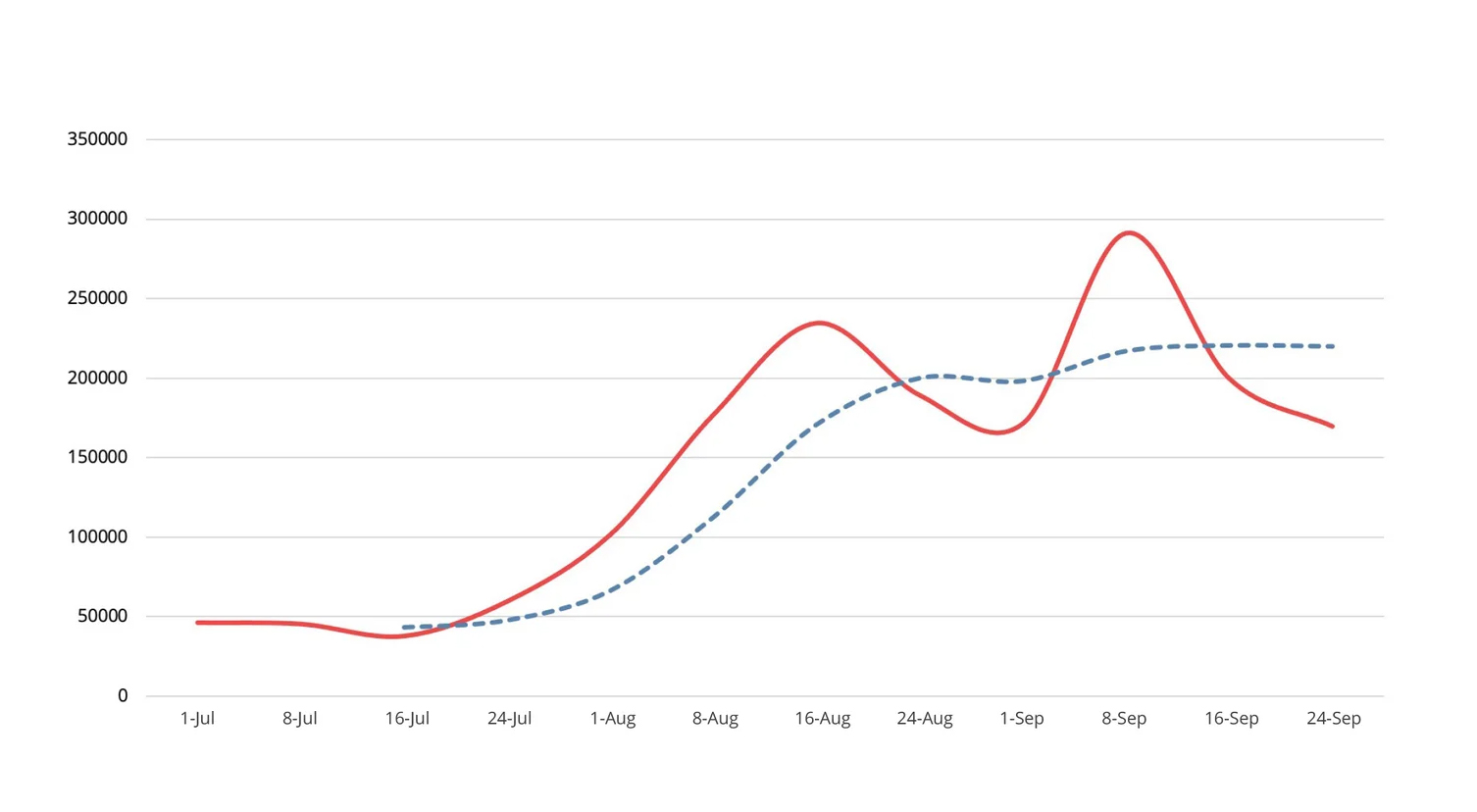
Detection, Q3 2021The increase in botnets can likely be attributed to Q2 2021 being one of the least active quarters we’ve seen.
How to Combat
Step up your efforts to stop botnet activity, which is usually detected post-infection. We recommend detecting malicious activity and quarantining devices to minimize botnet spread throughout the network.
Botnets
As predicted in Q2, ZeroAccess Botnet has resurged. While the botnets themselves are not new, XorDDOS and BadRabbit are two new additions.
Total Events
Unique Variants
Total Activity
Exploits
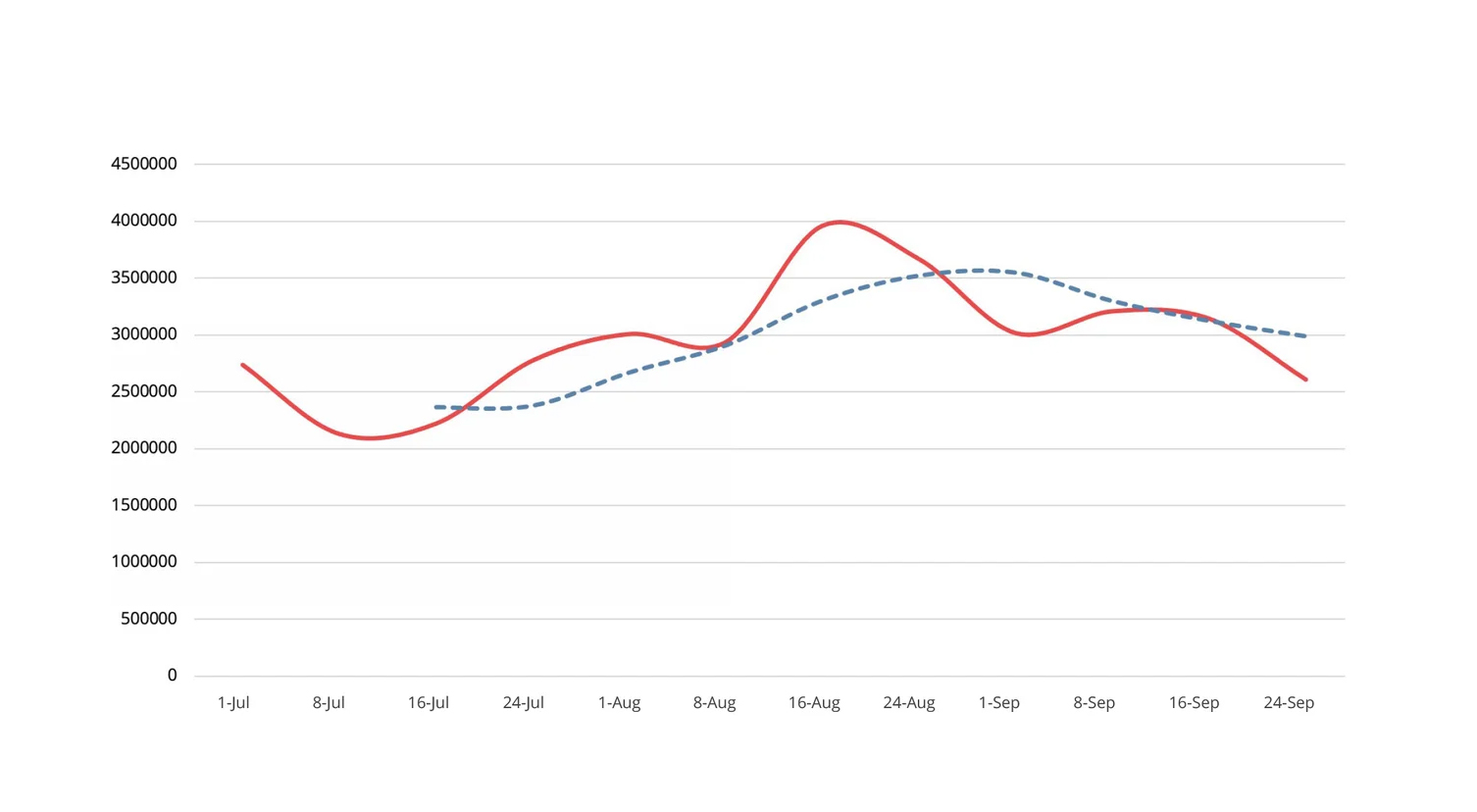
Detection, Q3 2021Exploit activity increased when compared to Q2 data, and threat actors focused on targeting perimeter devices.
Exploits
When reviewing exploit attempts against protocols, NetBIOS was the most attempted protocol again as seen in previous quarters, followed by SSH.
How to Combat
Stop exploits before they do harm by patching systems and security monitoring to thwart attackers and decrease risk.