Interactive Report Summary
Q3 2022 Threat Report
Top Findings at a Glance

Industry Spotlight: Healthcare
Healthcare organizations deal with a wide variety of sensitive and personal data, and they need operations to run flawlessly because lives are literally on the line if there is any disruption.
Threat actors know if they can launch an attack, the pressure on these organizations skyrockets, making them more inclined to pay out during a ransomware attack. In addition, personal identifying information (PII) is valuable on the dark web markets.
Top healthcare threat actors include FIN4, Orangeworm, Deep Panda, APT10, APT18, APT41, APT1 and APT29.
Methodology
How Nuspire produces its threat intelligence
Hover over tiles to learn more
Q3 2022 in Review
July through September
Total Events
Unique Variants
Total Activity
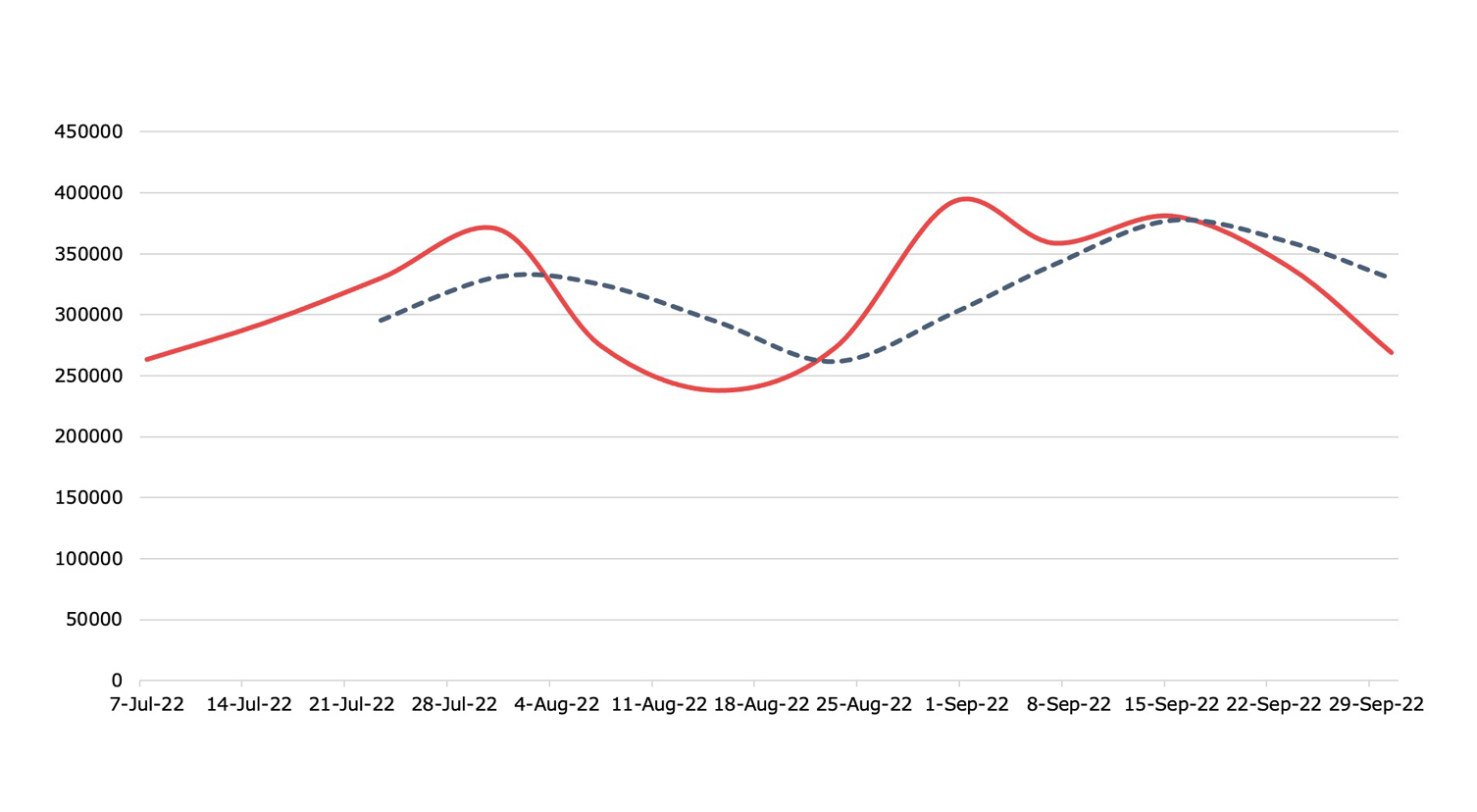
Malware
Detection, Q3 2022Across Nuspire managed and monitored devices, there was a decrease of 15.73% in total malware activity compared to Q2 2022
How to Combat
To strengthen your defenses against malware activity, you’ll need to adopt a multiprong approach including endpoint protection platforms and cyber awareness training.
Malware
While we observed a decrease in malware activity when compared to the previous quarter, it’s important to note that malware usage is still high. In fact, Kryptik trojan malware variants increased 236.22 percent in Q3. Kryptik is distributed to victims through phishing campaigns or when victims visit malicious sites. Focused on stealing information, this malware searches for and steals credentials from users’ browsers and applications. It also can steal cryptocurrency wallets, files and SSH keys.
Total Events
Unique Variants
Total Activity
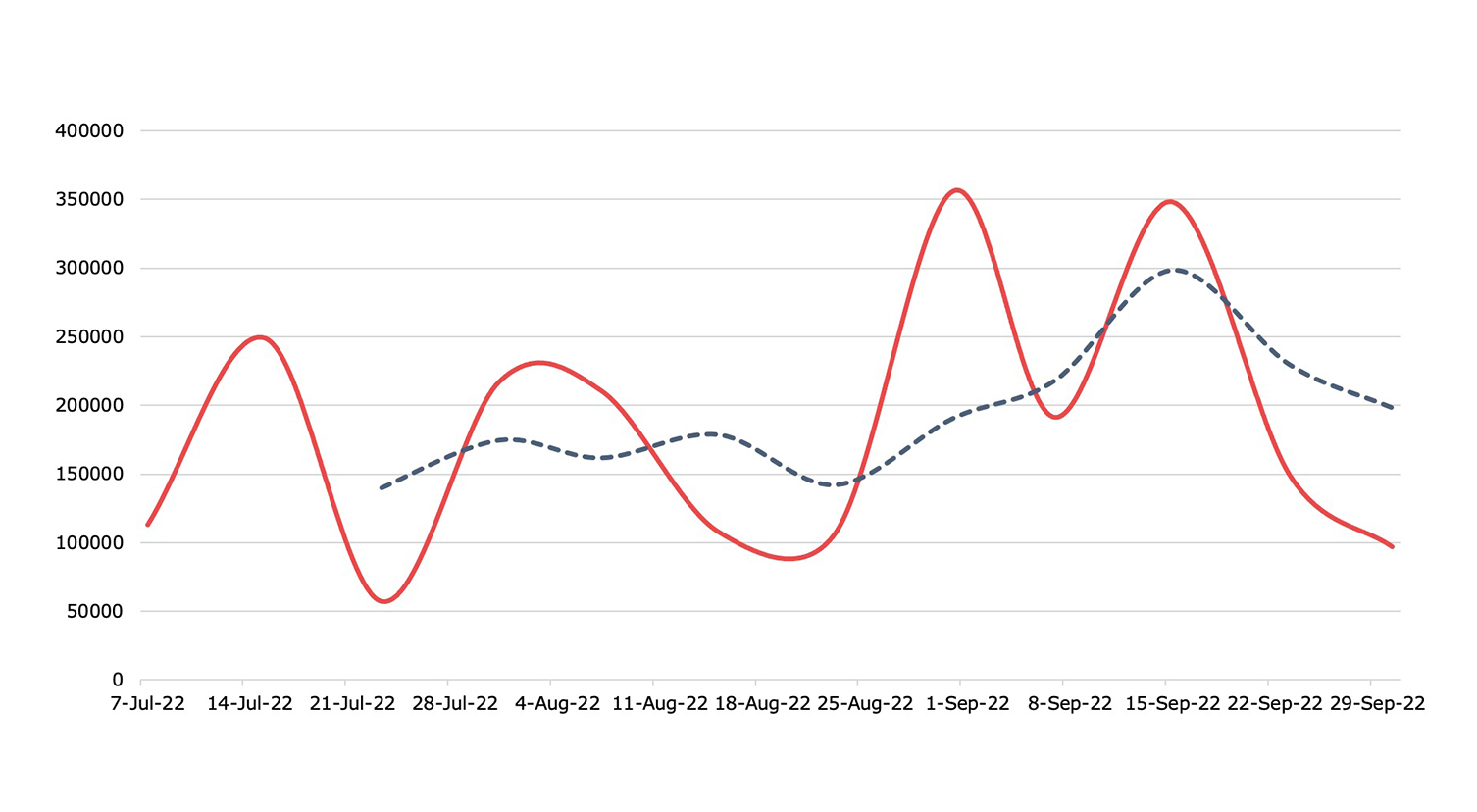
Botnets
Detection, Q3 2022Nuspire saw an increase of more than 35% in botnet activity
How to Combat
Step up your efforts to stop botnet activity, which is usually detected post-infection. We recommend detecting malicious activity and quarantining devices to minimize botnet spread throughout the network.
Botnets
Torpig Mebroot maintained its spot at the top of our list of most active botnets; however, we also so a resurgence of older botnets, including Xtreme RAT. Xtreme RAT is a remote access trojan first witnessed in 2010. It has multiple capabilities such as stealing data, manipulating processes and services, worming capabilities, keylogging and more. Typically, Xtreme RAT is spread via phishing or attached maliciously to applications that may include fake driver updates, pirated software and games, and free software.
Total Events
Unique Variants
Total activity
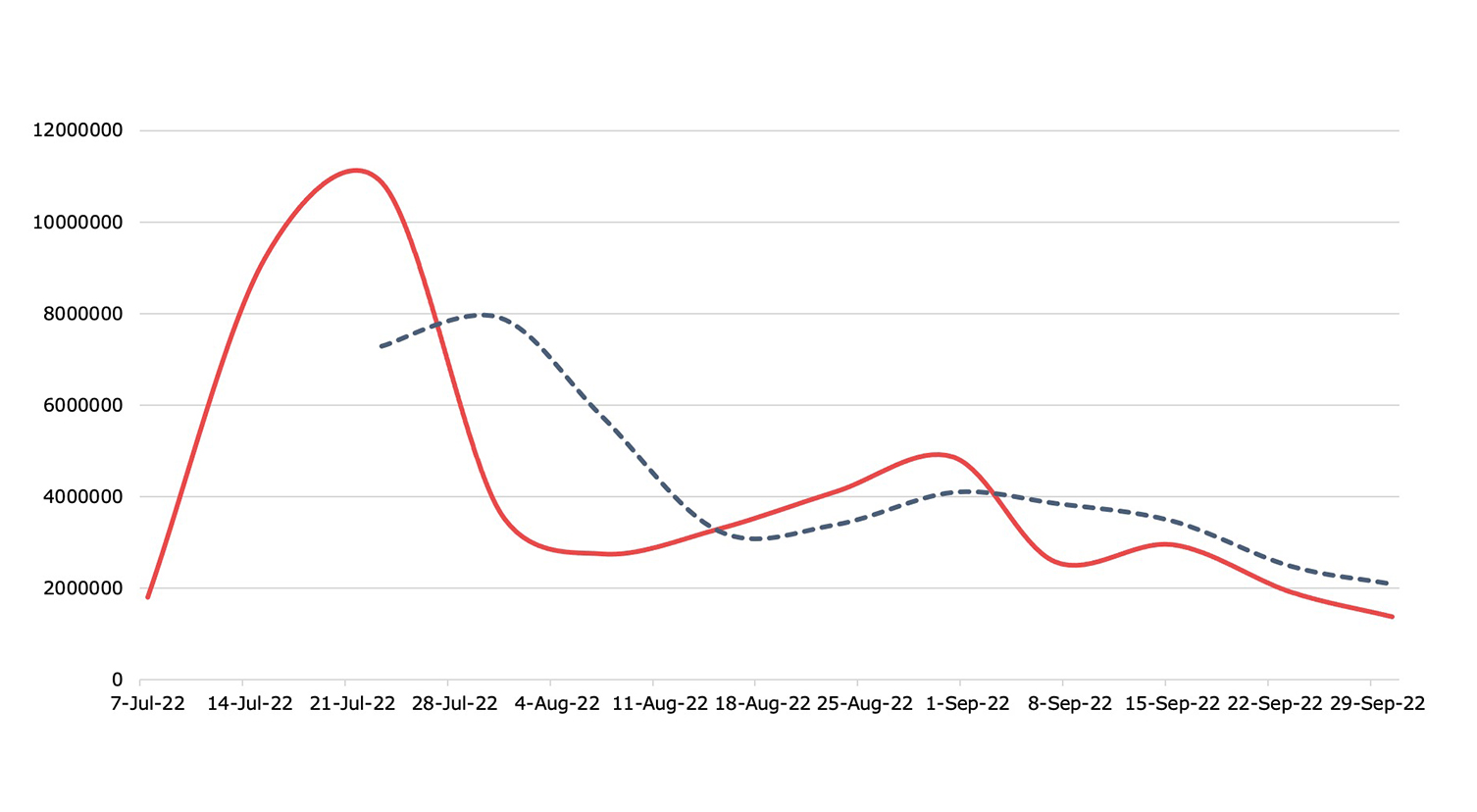
Exploits
Detection, Q3 2022Exploit activity grew slightly, continuing the heightened levels we saw in Q2
How to Combat
Stop exploits before they do harm by patching systems and security monitoring to thwart attackers and decrease risk.
Exploits
Threat actors continue to leverage brute forcing and newly-announced vulnerabilities to earn their pay. Nuspire detected a steady stream of attempts against the VMware Workspace ONE Access and Identity Manager vulnerability, and expects to see this continue given its important role in SSO, MFA and more.