Interactive Report Summary
Q3 2024 Cyber Threat Report
Top Findings at a Glance

Industry Spotlight: Professional & Technical Services
The Professional & Technical Services sector, including law firms, accounting firms and consulting agencies, has overtaken manufacturing as the most targeted industry by ransomware in Q3. These organizations handle sensitive data, making them prime targets for ransomware operators, who now commonly use double extortion tactics. With average ransom demands of around $2.5 million, the pressure to avoid reputational damage is high, forcing many to pay. The lack of robust cybersecurity measures leaves many of these firms vulnerable.
Methodology
How Nuspire produces its threat intelligence
Hover over tiles to learn more
July THROUGH September
Q3 2024 in Review
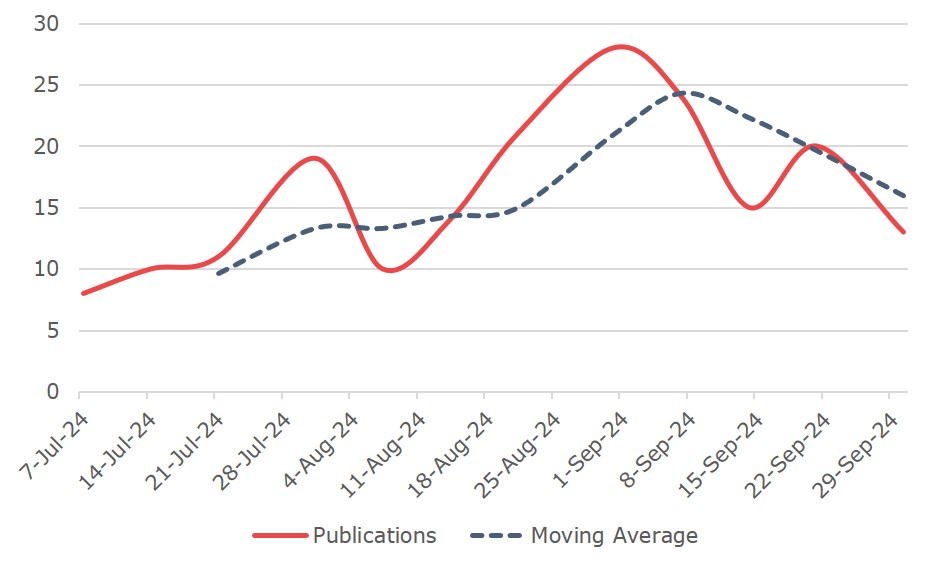
Total Ransomware Publications
Publications Averaged Per Week
Increase In Publications
Ransomware
Detection, Q3 2024Ransomware publications increased by 8.06% in Q3, with RansomHub dethroning LockBit as the top ransomware group.
How to Combat
To fortify defenses against ransomware, organizations should implement robust endpoint detection and response (EDR) systems, conduct regular data backups and enhance cybersecurity awareness among employees. These measures are crucial for preempting attacks and mitigating their impact.
Ransomware
In Q3, ransomware extortion publications increased, with RansomHub emerging as the new leader in ransomware activity, overtaking LockBit, which saw a significant drop in extortion attempts. Despite increased law enforcement actions, ransomware groups continue to evolve their tactics, employing double extortion to pressure victims into paying ransoms. RansomHub’s affiliates have targeted various industries, focusing on critical infrastructure, healthcare and financial services.

Total Marketplace Listings
Listings of Stolen Browser Data
Decrease in Total Listings
Dark Web
Dark web marketplace listings decreased by 5.41%, but Lumma Stealer returned as the top infostealer.
How to Combat
To combat dark web threats effectively, it is essential to implement comprehensive cybersecurity measures, such as advanced threat detection systems and stringent data protection protocols. A dark web monitoring service can enhance these efforts by continuously surveilling dark web marketplaces. Regular monitoring is crucial for early detection of potential threats and swift response to protect sensitive data.
Dark Web
While dark web marketplace listings saw a slight decline, there was a resurgence of infostealer activity, with Lumma Stealer reclaiming its position as the leading malware variant sold on these platforms. Infostealers like Lumma allow cybercriminals to harvest sensitive information, including credentials and financial data, which are quickly sold to other threat actors. The drop in listings was largely driven by a decrease in stolen browser data offerings, but threats of identity theft and account compromise remain high, particularly as email and credit card access listings are still prevalent.
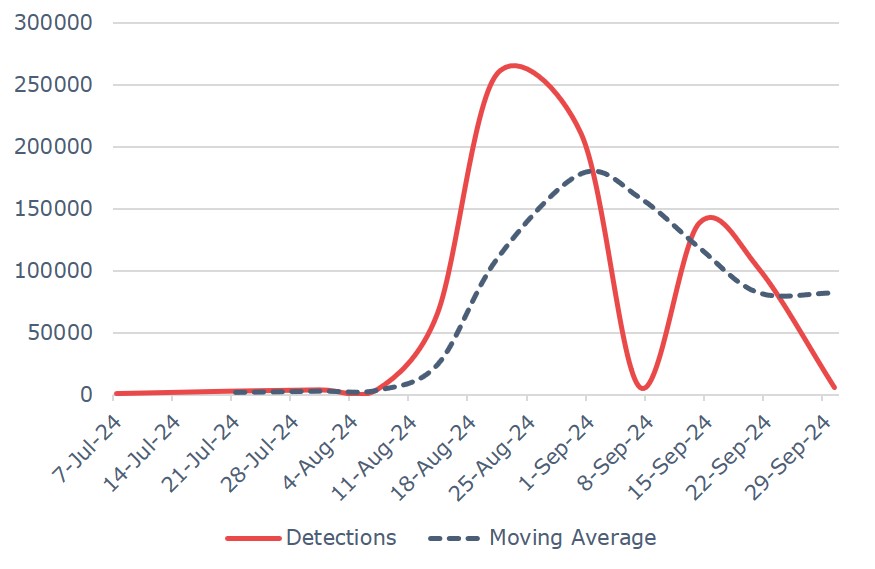
Total Exploit Events
Unique Exploits Detected
Increase in Activity
Exploits
Exploit attempts surged by 50.96% in Q3, with a significant focus on VPN vulnerabilities.
How to Combat
Preventing exploits involves rigorous system patching, using firewalls with intrusion prevention systems, and staying informed through security news and vendor bulletins. Proactive security measures are vital to thwart attackers and reduce the risk of breaches.
Exploits
Exploit activity skyrocketed in Q3, with a marked increase in attacks targeting VPN technologies, such as Fortinet’s SSL-VPN heap buffer overflow vulnerability (CVE-2022-42475). Threat actors continue to exploit long-standing vulnerabilities in remote access technologies, taking advantage of organizations that have not yet patched their systems. These vulnerabilities provide cybercriminals with direct access to critical systems, enabling data exfiltration, malware deployment and further attacks.
Stay Vigilant
Q3 2024 saw a rise in ransomware publications, a shift in dark web marketplace trends with new types of data being targeted, and a surge in VPN exploit attempts, highlighting the growing sophistication of cyber threats. While dark web listings slightly declined, the return of Lumma Stealer and the spike in VPN vulnerabilities highlight how threat actors are evolving their tactics to bypass traditional defenses.
To combat these sophisticated threats, organizations need a comprehensive approach that includes services like endpoint security, dark web monitoring, meticulous patch management, and proactive vulnerability assessments. These efforts can be further augmented by AI-driven intelligence and enhanced visibility, enabling organizations to more effectively detect and respond to threats, strengthen their defenses and stay ahead of cybercriminals’ evolving tactics.