Interactive Report Summary
Q4 and Full-Year 2024 Cyber Threat Report
Top Findings at a Glance

Ransomware Spotlight: Clop
Methodology
Hover over tiles to learn more
OCTOBER THROUGH DECEMBER
Q4 2024 in Review
Q4 2024 was marked by a surge in ransomware and exploit activity, a shift in dark web trends.
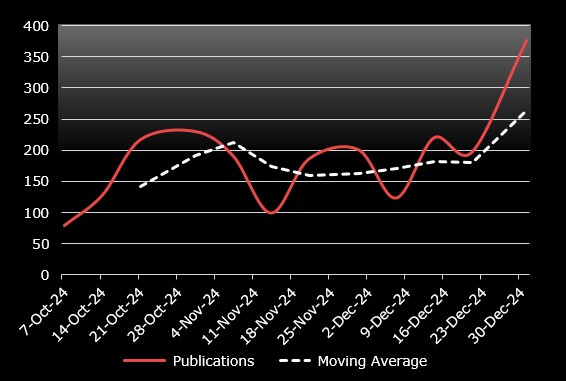
Total Publications Q4
Total Publications 2024
Change from Q3
Ransomware
Ransomware Detection, Q4 2024Total ransomware publications in Q4 reached 2,247, reflecting a 46% increase from Q3. Across 2024, there were 8,156 total ransomware publications, highlighting the growing impact of ransomware threats.
How to Combat: Defend against ransomware with regular backups, endpoint protection, zero-trust security, and employee training. Keep systems patched and use advanced threat detection to stay ahead.
Ransomware
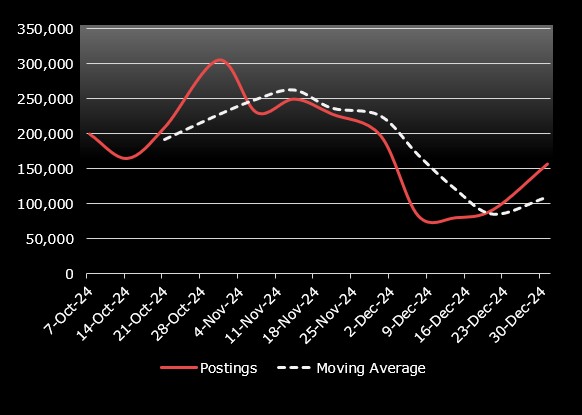
marketplace listings in 2024
fraud-related topics discussed in 2024
Stolen Credential-related topics discussed in 2024
Dark Web Activity
In Q4 2024, while dark web marketplace listings decreased, malicious activity shifted to private channels with a significant surge in discussions about fraud, hacking, and stolen credentials. How to Combat: Implement a layered security approach including dark web monitoring and employee training to mitigate phishing risks and protect sensitive information.
Dark Web Activity
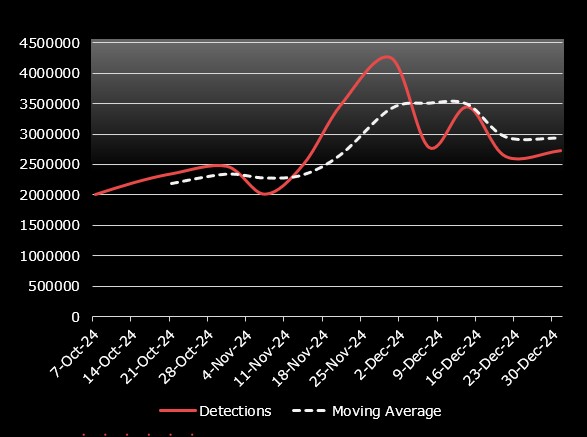
Total Events 2024
Unique Variants
Total Activity
Exploits
Q4 2024 In Q4, exploit activity surged by 72%
How to Combat
Stop exploits before they do harm by patching systems and security monitoring to thwart attackers and decrease risk.
Exploits
Stay Vigilant

As Nuspire's Director of Security Operations, Justin Heard is at the helm of the company's key security initiatives, encompassing incident response, threat hunting and cyber intelligence. With over 16 years of experience in cybersecurity, including roles such as threat hunter, incident commander and intelligence analyst, Justin has a deep understanding of the cybersecurity domain. His leadership is instrumental in bolstering Nuspire’s defenses and adapting to the rapidly changing landscape of cyber threats.
Before his tenure at Nuspire, Justin enhanced his skill set in the defense sector, serving as a network administrator and security engineer. Justin has an associate degree in Computer Networking Systems from ITT Tech.

Josh is a Cyber Threat Analyst at Nuspire who works closely in organizational threat landscapes, curating threat intelligence, and authoring Nuspire’s Quarterly Threat Landscape Report. Josh is currently pursuing his master’s degree in Cybersecurity Technology. Previously he served with the U.S. Navy as an Operations Specialist with 14 years of service. Josh has been quoted in Forbes, CSO Online, Channel Futures, Dark Reading, and others.